This article lists some of the best dark web websites you can visit securely. Some of these sites are very helpful (but unseen as Google doesn’t show them), while others are just for fun. BidenCash and other exit-scam markets such as Torzon and Kingdom Market collapsed between 2022 and 2024. They used “free data dumps” and emotional marketing to build trust before vanishing—an enduring lesson in the risks of social engineering. However, any illegal activities conducted on the dark web, such as purchasing illicit goods or engaging in criminal behavior, are still punishable by law.
Arrest And Trial Of Ross Ulbricht
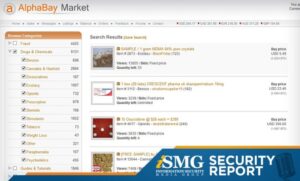
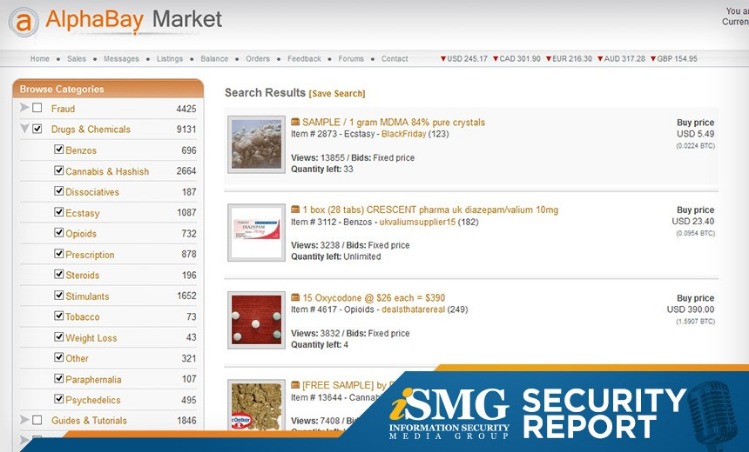
Dark web websites are pages that exist on a part of the internet that isn’t indexed by traditional search engines like Google. Also known as deep web sites, these pages typically have URLs ending in .onion and are only accessible through special software like the Tor Browser. Most darknet market administrators are now tightening access controls.

Implications For Security Leaders
There is no need to visit darknet marketplaces yourself to know whether your data was leaked. Some vendors offer services to help people “clean” illegally obtained funds using cryptocurrency and fake transactions. They mix and transfer funds through various privacy wallets and escrow services to hide the original source and make the illicit transactions harder to trace. This can include everything from full names, email logins, and passwords to credit card details, social security numbers, and bank account information.
Defenders must integrate machine learning for real-time anomaly detection in encrypted traffic. When your data is found on the dark web, it means that you’ve been compromised. Therefore, you need to start by changing your passwords, and you need to notify your credit card or bank provider.
Stay Up-to-date With KELA News And Insights
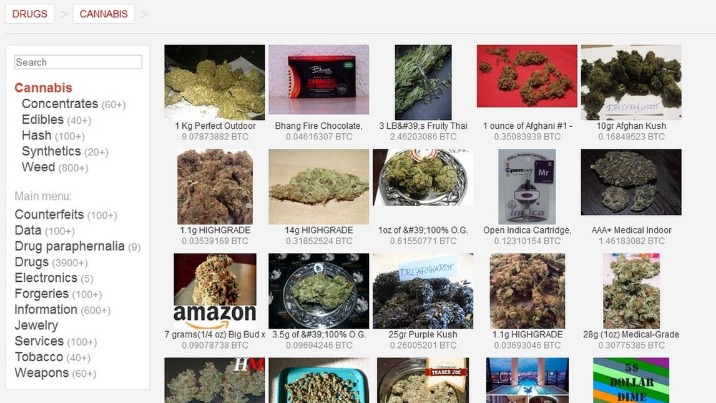
Patterns recommended to avoid include hiring hitmen like Dread Pirate Roberts, and sharing handles for software questions on sites like Stack Exchange. Using TAILS is yet another security measure that protects your online identity on the dark web. It is a specific Debian-based version of Linux software that leaves no traces of the user activity or the operating system on the computer. It uses the Tor network because it is a popular network that helps to circumvent censorship and online surveillance. Cybercriminals on the dark web marketplace always look for new victims to target them with scams or infect their devices with malware, spyware, or adware.
Key Features
It has a proprietary onion site in the Tor network to give you safe access even if your country restricts VPN usage. The most interesting thing about NordVPN is its built-in Onion over VPN feature. It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. For this reason, you must watch out and avoid opening anything that looks suspicious to you.

Dark Web Tools And Services
It was initially created to provide additional security and eliminate cryptocurrency theft. It’s a wallet, explorer service, not a dark web marketplace itself, but still a helpful resource. Darknet marketplaces in 2025 illustrate a resilient and evolving underground economy. Major active platforms include Abacus, Russian Market, BriansClub, and Exodus. Law enforcement takedowns, such as Archetyp, demonstrate both impact and adversary adaptation. For cybersecurity professionals, focusing on payment methods, vendor migration, and marketplace specialisation offers the most effective path to actionable intelligence.
Riseup is available on the surface web, but its presence on the Tor network extends its privacy benefits by letting you use its services without exposing their real-world identities. You can access encrypted email services through the onion site without getting tracked. You can access DuckDuckGo on the surface web, but a Tor version is also available.

Darknet Market Prices
This option is ideal for digital products, domestic shipping, and transactions with established, high-reputation vendors. We strongly encourage disabling JavaScript within the Tor browser when accessing Black Ops Market. This practice minimizes vulnerabilities and protects users from potential phishing attacks, browser exploits, and tracking attempts that could compromise your anonymity and security. In addition to its emphasis on stolen credentials, 2easy Market offers a variety of cybercrime tools, such as hacking services, exploit kits, and other resources for conducting cyberattacks. Unlike many other dark web markets, Cypher does not require buyers to deposit cryptocurrency upfront, which reduces the risk of exit scams.
More often than not, law enforcement is targeting the sellers more than the buyers. Still, it isn’t unheard of for people to be arrested for buying drugs on DNMs. As the DNM builds a small pool of users and sellers, it will snowball into a lucrative operation IF the service remains reliable and secure. Besides ever increasing hosting costs, the site will have to contend with authorities, attacks from hackers, and the occasional disgruntled market administrator.
Criminal Hacking Services
- At KELA, we help you identify and mitigate risks by providing actionable intelligence from the darknet.
- In many countries, strict laws limit who can legally buy, own, or carry firearms.
- It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome.
- “A lot of people use it in countries where there’s eavesdropping or where internet access is criminalized,” Tiquet said.
- These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies.
Last week, one of the dark web’s most prominent drug marketplaces—Archetyp—was shut down in an international, multi-agency law enforcement operation following years of investigations. It was touted as a major policing win and was accompanied by a slick cyberpunk-themed video. Also, set up two-factor authentication (2FA) to add an extra layer of protection in case someone manages to figure out your password.

This handy feature monitors the dark web for signs that your login details or other personal info have been leaked. However, the dark web is so complex and vast that if law enforcement takes down one market, it pops up elsewhere. For instance, after the closure of Genesis Market, its website came back after a few weeks. If someone has the market’s code to the infrastructure, no matter how much effort law enforcement puts in, it will keep coming back on another server or can be built again with the same branding. What’s more concerning is that most of the time, we don’t know about these flaws, and by the time we try to fix them, we come to know it’s too late.
- In March 2000, an Irish grad student named Ian Clarke created the software application, Freenet.
- Drug dealers can sell to customers across the world, not just locally.
- It’s a popular choice for users worried about online surveillance and data collection.
- It is easily accessible by the general public and requires no special configuration.
- Abacus alone represented nearly 5 per cent of total DNM revenue, underscoring the ongoing scale of underground commerce.
Tor Metrics is a set of tools and data provided by the Tor Project that offers insights into the performance, usage, and activity of the Tor ecosystem and its nodes. Besides monitoring and improving the network, the data can be used to detect possible censorship or attacks. Due to the privacy-forward ethos of the Tor project, Tor Metrics stresses that the data it collects must not undermine the anonymity or security of the network.