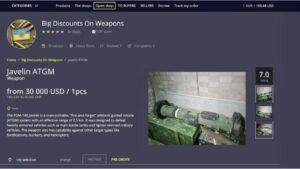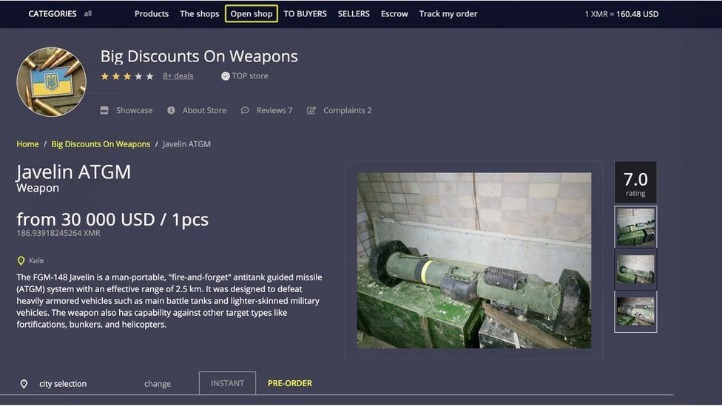
By the mid-2020s, darknet websites continued as facilitators of international cybercrime. In addition to proffering illicit materials, many such sites allowed money laundering and other illegal financial services. Another evolution was the involvement of national governmental agencies and personnel in these illegal activities.
Is Claude Safe And Secure In 2025?
A robust antivirus can help block malware and other online threats, even on the dark web. Radar Rundown Hiding your IP address is one of the best ways to protect your online activities from … Radar Rundown Private search engines use the metasearch or proxy search model and the proprietary cr… The dark web is a part of the deep web that contains websites not included in the mainstream search engine index. It is a good website for finding out which websites are currently working.
- While people and organizations do host legitimate and useful sites on the dark web, it’s still best to tread cautiously.
- Civil libertarians wondered whether there was more to the Silk Road shutdowns than the FBI revealed.
- It’s not as massive as Abacus, but quality’s on point—vendors deliver, and the community’s buzzing on Dread about it.
- Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people.
Tor Browser: Accessing The Darknet
It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. For this reason, you must watch out and avoid opening anything that looks suspicious to you. You risk being targeted for attacks if you explore the dark web without protection. The threat can extend to your entire network of devices connected to the internet. Since malware lingers across the dark web, your device can easily become infected, even if you are an unsuspecting user.
Dark Web Marketplaces In 2025
Darknet websites were nearly invulnerable to this strategy, since they accepted communications only from Tor. However, the site visitors’ computers may have contained identifying information, which could be revealed inadvertently in an error message. Tor was developed in the 1990s by the US Naval Research Laboratory. The name was an acronym for The Onion Routerreferring to the layers of encryption that were added and then peeled away as a message passed through the system. In 2004two years after Tor went onlinethe laboratory made the software available for free to any Internet user.
Is The Dark Web Illegal?
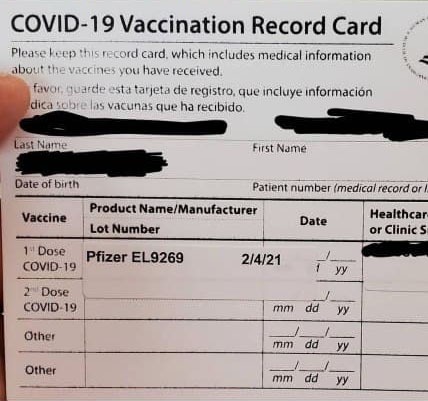
The dark web is a part of the internet that you only step into with a specific tool (Tor, more on this later in the article). Though people usually think of dark websites as the wrong online place, that’s not the complete truth. Although the underground internet world is rife with everything bad, it also hosts positive elements. This particular marketplace surfaced in the middle of 2017 and had remained active ever since. However, it’s worth noting the website does not contain multisim like other marketplaces do and don’t force vendor PGP, but there is 2FA to help you stay protected while buying online.
More On Tor Onions
The Tor Onion Browser is essential for accessing the dark web, designed for user anonymity. Unlike the regular internet, the dark web doesn’t use standard URLs or search engines. Instead, sites have complex .onion addresses, making them difficult to find without the exact URL. The marketplace has an intuitive interface and offers powerful search tools that make it easy for you to find products from both local and international sellers. All vendors are vetted before they are allowed to sell, so it makes sure of trust and quality.
What Kind Of Content Is On The Dark Web?
Most people start by using the Tor Browser, which hides your IP address. Some markets are invite-only or have strict registration rules to keep out scammers and law enforcement. Its Dark Web mirror ensures that even when governments force ISPs to block its services, anybody who relies on its services can leverage Tor to continue communicating with friends and family. Privacy advocates frown upon it because of the way it harvests data and profiles users. These concerns are valid because using Facebook undoubtedly exposes users to some of the highest levels of surveillance capitalism anywhere on the web.
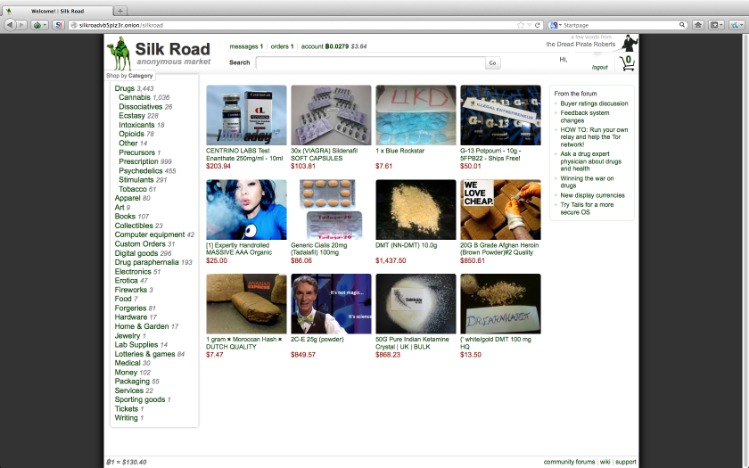
- The fact that it discusses vulnerabilities, legal tools, data leaks, and malware attracts prominent threat actors constantly.
- Despite multiple takedown efforts by law enforcement and security researchers, Brian’s Club has resurfaced repeatedly and continues to add new stolen credit card data.
- STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity.
- Some popular search engines that can help you explore hidden content and anonymize your web traffic include DuckDuckGo and Ahmia.
- Dark markets often employ end-to-end encryption for communication between buyers and sellers, enhancing security and privacy.
Perhaps one of the major attraction factors of these forums is undoubtedly anonymity. Cybercriminals want to carry out their illegal activities without detection by law enforcement agencies and other authorities. In contrast, sites hosted on the dark web can only be accessed via onion routing with Tor, or another dark web browser. LifeLock Standard helps safeguard your personal information, accounts, and identity. There are media websites on the dark web—both legitimate and illegitimate—that allow users to access digital media outside the highly monitored surface web.
However, if you must buy items from the dark web, set up a secure, encrypted email with CounterMail or ProtonMail. For more information, read more about the most secure email service providers in my other post. The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as “.onion”, which means that the URLs are only accessible by Tor users. Hacker services against banks and other financial institutions are offered there. We’ve also previously mentioned the “dark users” that use the dark web for illegal reasons, but the less said about them, the better.

Besides, LeakBase functions as a marketplace and as a discussion center where cybercriminals exchange compromised data. Moreover, it features a high number of stealer log data that includes credential pairs like passwords and email combinations. Wizardshop.cc was established in 2022, and offers a wide range of leaked CVVs, database dumps and even RDPs. In the past 6 months, the site has increased the volume of cards sold, placing itself as one of the top sites selling credit cards today. The site has a unique news section, where the admin updates the buyers about new leaks and dumps, the source of the dumps, structural site updates and more.
Onion sites are dark web sites that can only be reached through online routing via Tor, in which encrypted data passes through multiple nodes before reaching its destination. Decrypting the data involves peeling back layer upon layer of encryption, hence the “onion” analogy. ProtonMail is an email service that uses end-to-end encryption, making your email accessible to you and only you. The service retains no copies of any data that passes through a ProtonMail account.
In opennet mode, the network will automatically assign you to other users on Freenet’s network. As I mentioned previously, the dark web is quite popular with journalists, political bloggers and news publishers, and others who run the risk of imprisonment in countries like Iran and others. Now that you’ve completed the download, it’s time to install the Tor browser on your device. (The installation instructions that follow are for the macOS platform, I’ll mention where it’s different for Windows.) Simply double-click the downloaded file in your download folder. So, once you’ve activated your VPN and your privacy is secured, it’s time to visit Tor’s official download page. Make sure that when you download the Tor file, it’s from their official website.