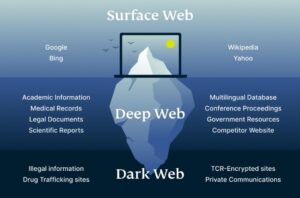
Millions of customers’ personal data, including names, addresses, bank account and credit card account information, and many other forms of sensitive data. The users of the dark web are typically aiming to block governments from snooping on them. This can often be for political reasons, but also because they may be involved in illegal activities, such as the ones listed above. The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose. That means that only 0.024% of all the known pages are findable in Google’s search engine.
In contrast, sites hosted on the dark web can only be accessed via onion routing with Tor, or another dark web browser. Users can explore onion sites easily and search for content without having to know any specific onion links in advance. You’ll keep your identity private while getting results for various Tor websites, forums, and marketplaces.
FAQs About The Dark Web And The Websites That Live On It

DuckDuckGo is a privacy-focused search engine that works as Tor browser’s primary search engine. It doesn’t track searches or store personal data, making it a strong option for users seeking more anonymous private browsing. However, DuckDuckGo doesn’t index dark web content — it only accesses surface and deep web sites through Tor. Talking about copycats and potential risks, due to its high risk and low signal-to-noise ratio for legitimate content, we advise beginners and privacy-conscious users to avoid The Hidden Wiki. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites. Because dark web pages generally aren’t indexed, you can’t find them using traditional search engines, but some search engines like DuckDuckGo may help you navigate the dark web more easily.
Threat actors target organizations based on exposed credentials, stale access points, or misconfigured assets advertised or sold. A lot of this information is inexpensive and readily available — opening the door to attacks. Experienced blogger with a strong focus on technology, currently advancing towards a career in IT Security Analysis. I possess a keen interest in exploring and understanding the intricacies of malware, Advanced Persistent Threats (APTs), and various cybersecurity challenges. My dedication to continuous learning fuels my passion for delving into the complexities of the cyber world.

Encrypted Communication Tools
It works by sending internet traffic through volunteer-operated nodes all over the world. This network of over 6,000 relays hides your location, thus protecting you from online surveillance and third-party tracking by your websites. The Dark Web is the part of the deep web that is not indexed by search engines, like Google or Bing.
Tor And The Onion Browser
With the above dangers, it’s imperative to tread carefully as you step into the dark web. Stay safe and informed as you explore the deeper layers of the internet. Generative AI is being used to fabricate synthetic identities, including deepfake voices, forged credentials, and AI-generated backstories. “Identity fraud is enhanced through synthetic persona generation and deepfakes, aiding criminals in bypassing know your customer (KYC) and biometric checks,” says Kroll’s Currie.

onion URL Structure
It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship. The anonymity provided by onion routing comes at the cost of slowing your internet considerably.
Follow these best practices every time you venture onto the dark web. Internet shutdowns affected 4.78 billion people in 2024 alone, as governments from Iran to Myanmar throttled access during protests and elections. In that climate, the dark web’s anonymity tools serve as a digital lifeline for journalists, whistleblowers and ordinary citizens who need uncensored information. While Google Chrome is popular, it’s also known for collecting significant amounts of user data. Alternative browsers like Brave, Tor Browser, and Mozilla Firefox will allow you to keep your online activity private. Every message, search, and stored file on a US-based platform exists in a system designed to watch, categorize, and sometimes hand over your information with ease to authorities.
Dangerous Software
Since Tor Onion Services is by far the most popular (and therefore most generally useful) dark web, we’ll focus on that here. An advantage is that web pages (and other data) can be available long after the original host has disappeared. However, if no one accesses data for a long time, it can disappear (this works much like BitTorrent, where files that aren’t actively seeded become de-indexed over time).
DuckDuckGo (Dark Web Version)
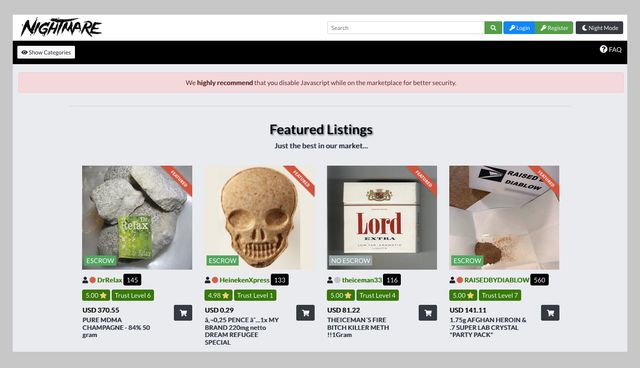
The first website on our list is, allegedly, the largest repositories of scientific papers on the dark web. Careful though, because many ‘users’ reported malicious links and redirects while perusing Sci-Hub. All the dark web websites we’ve listed in this article will not be of much use to you unless you know how to access and use the dark web. So, before accessing the dark web, be sure you know how to do so safely and anonymously. In some ways, dark web websites offer more browsing freedom, but the lack of safeguards can leave you exposed to hackers, malware, and other online threats, like viruses or other malware. The lack of regulation leaves the dark web rife with offensive content and unsafe websites.
Don’t Stick Your Nose Where It Doesn’t Belong
For searching within the dark web, specialized tools like Torch are better, as they specifically index .onion sites and hidden content. Deep Search is an open-source dark web search engine designed to index and explore onion space, the hidden services within the Tor network. Known for its accuracy, Deep Search stands out by delivering precise and useful results, avoiding the spammy links commonly found on similar platforms.
Next to antivirus software, find and select a quality VPN for surfing the deep web. Virtual Private Networks (VPNs) keep you safe when surfing the internet in various ways. The most obvious way is by hiding your computer’s IP address and assigning you a new one, usually a different region. If the antivirus confirms that a file poses any danger to your device, it warns you.
Forward Digital Software Website
Since the dark web is a hidden and uncontrolled part of the web, there is a high amount of malware infections present there. As a result, you should avoid opening unfiltered sources, torrent sites, and dark web links unnecessarily and downloading every file you come across. Immediately close your entire Tor Browser window (not just that active tab). Note that engaging with the content in any way is not only distressing but could also put you at legal risk.
Why Is Tor So Slow?
- Analysts now project global cybercrime damages will hit $10.5 trillion annually by year‑end 2025, underscoring the dark web’s outsized impact on the broader Internet economy.
- In that case, there is a high chance that your data will become accessible to cybercriminals.
- Instead, it routes your connection through a series of encrypted servers, or nodes, to maintain anonymity for both users and websites.
- Some websites (like How-To Geek) will obey your browser’s dark theme and change their theme accordingly, but many don’t.
- Its user-friendly interface and reliable protection are unmatched.” — Jamie L.
- Onion.name is a dark web resource that helps make sense of the mess of letters and symbols that usually form the darknet sites.
He was formerly the Chief Financial Officer and a principal shareholder of Apollo Solutions, Inc., which was acquired by CNET Networks. Individual sites on the dark web look much like they do on the regular web, though a lot of them are a bit more rough around the edges. (Presentation and polish isn’t quite so important on this part of the internet.) Click on any website link, and it’ll appear on screen, with its address at the top.
One of the biggest problems cybersecurity teams face isn’t a lack of tools — it’s too many alerts. Anyone can access the dark web, and it’s not that complicated to do so. Just remember, if you want to explore the dark web, be very careful. This allows you to use the computer without the risk of corrupting your computer’s normal operating system with viruses or malware.