Every plan includes up to $1 million in identity theft insurance for each adult on your plan, along with a U.S.-based customer care team ready to help you recover your identity. Each plan comes with Dark Web monitoring, social media monitoring, SSN monitoring, court records monitoring, and medical data reports. Yet, despite the positives, the primary use of the Dark Web is to buy and sell stolen and illegal goods and services — and, increasingly, personal data. Submit your information and an eSentire representative will be in touch to discuss how eSentire can help protect your organization with Dark Web Monitoring services. Get stronger correlation of external and internal risk indicators for better context into the potential cyber threat.
In conclusion, dark web monitoring is not just about detecting threats; it’s about taking proactive steps to protect personal and organizational data from the increasingly sophisticated tactics of cybercriminals. Whether it’s protecting against identity theft, complying with regulatory standards, or safeguarding intellectual property, dark web monitoring plays a crucial role in the broader context of cybersecurity. Dark web monitoring software is a tool that can scan, identify, analyze, and report activities on the dark web that are relevant to your organization. Since this part of the internet is not indexed by standard search engines, threat actors often use it for illicit activities including buying and selling stolen sensitive information. Flare enables you to automatically scan the dark, deep, and clear web for leaked or stolen account credentials. Access to dark web and deep web sources tools to deal with tactics, techniques and procedures (TTPs), vying to steal your personal or business information that come with being active on the Dark Web.
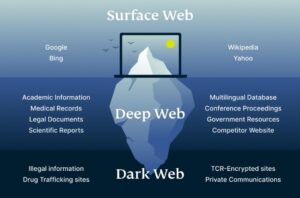
Is The Dark Web Illegal?
There is no point in scheduling a total scan of the Dark Web say, once a month because as soon as credentials on your network are published, your business is exposed. The best Dark Web scans spot protected accounts as soon as their details appear on a Dark Web forum, enabling users and account administrators to change login credentials immediately. As such, Scout is a data loss prevention system and an insider threat protector as well as a threat-protection system. When a Dark Web threat is spotted, Scout raises an alert in the monitoring dashboard. It is up to the network administrator to shut down the traffic either manually or by deploying threat mitigation software. Effectively, this is a managed security service and it is a very high quality package.

Things You Didn’t Know About Telegram Cybercrime (Until John Hammond Showed You)
Because of the murky anonymity of the dark web, cybercriminals can surreptitiously buy and sell information illegally, like two people meeting in a dark alley to exchange cash for illegal goods. Cybercriminals sell personal information, credentials or asset access on the dark web. According to CrowdStrike’s Global Threat Report, adversaries continue to show that they have moved beyond malware. Of all detections indexed by CrowdStrike Security Cloud in the fourth quarter of 2021, 62% were malware-free. Open XDR with Agentic AI & machine learning that eliminates noise, enables real-time detection and response, and automatically blocks threats. My main question here is for basic monitoring such as x user credentials are on DW.
- It provides early warnings of data breaches, enabling faster incident response and reducing the impact of cyber attacks.
- Flare provides a cybersecurity platform that specializes in dark web monitoring and threat exposure management.
- Sixty-five percent of CISOs say their teams lack the skills for effective threat intelligence.
- Flare covers more than 4,000 cybercrime Telegram channels including those focused on combolists, stealer logs, fraud, and hacking.
- Cybercriminals often target PII because it can be used for various nefarious activities, such as identity theft, fraud, or even more targeted attacks such as spear-phishing.
- The dark web can be a hotbed of illicit activities, including the sale and exchange of various types of leaked information like internal communications, customer databases, intellectual property, trade secrets, etc.
Proactive Monitoring Can Help Reduce Your Risk
Once you’re on the Dark Web, you can communicate privately with others using encryption. KEY TAKEAWAYS Vulnerability management tools scan and detect weaknesses within the network that hac… It is advisable to use the best password managers that generate strong passwords and store them in a secure encrypted vault. Read along as we hand-picked some of the best Dark web monitoring services that work in 2025. Learn effective strategies for conducting threat hunting in your organization. Instead, your best bet is to change your passwords and open new financial accounts.
Web Hosting Company Increases Security Team Bandwidth With Up To 80% Decrease In Threat Research Times
Founded in 2001, the company’s mission is to hunt, investigate and stop cyber threats before they become business disrupting events. Monitor for compromised credentials for sale to the highest bidder, and detect sensitive data leaks with automated alerts. With ZeroFox Dark Web Monitoring, you’ll gain insight into attack planning and chatter to inform defensive efforts. Rely on our team of analysts to monitor your adversaries and engage with threat actors. We can obtain data samples, uncover motives, and help you deploy smarter cybersecurity workflows.

How Does Norton Find My Personal Information On The Dark Web?
Censys provides in-depth visibility into internet-connected assets, including the dark web. Identity Guard not only monitors your data, but it also alerts you when there’s a change in your credit report. Despite their reach, no dark web scanner can cover all the stolen data that exists across the entire dark web as a result of criminal activity. However, if you suspect your personal information has been compromised, a dark web scan can be a great resource to help ease your mind.
There are a few different types of dark web monitoring tools, each with a specific purpose. On the other hand, Dark Web crawlers and scrapers are used to crawl the darknets and collect data to help improve security or investigate potential threats. Outpost24 is a threat intelligence provider that offers a dark web monitoring solution as part of its cyber threat intelligence platform. Their solution helps organizations detect and respond to cyber threats by providing real-time visibility into malicious activities on the dark web. With Outpost24, businesses can enhance their cyber security posture by staying informed about potential risks and taking proactive measures to protect their data.
What Are Dark Web Threats?
Each of these categories represents data that is highly sensitive and valuable, both to the individual it pertains to and potentially to cybercriminals. That’s why it’s crucial to consider dark web monitoring as part of a comprehensive cybersecurity strategy. Cybersecurity service providers have a more precise definition of the Dark Web. A data breach, especially one that leads to the exposure of customer data, can severely damage a company’s reputation.

Intelligence X
Most businesses are left with a series of questions when they are asked how they can protect against dark web threats. Get ahead of breaches and mitigate scams faster by identifying mentions of your brand, assets, products, employees, and users across cybercrime forums, marketplaces, communication channels, and more. Identify emerging scams, including phishing kits targeting your brand, before they launch. With authenticated, account-level access to more deep and dark web channels, our solution provides comprehensive coverage and visibility into cybercriminal activity relevant to your organization. Experian offers Dark Web Surveillance through its Premium and Family memberships.
When the monitoring tool identifies potential threats, it displays them in a centralized dashboard and sends real-time alerts. These alerts prove invaluable to organizations as they can optimize their responses and implement the most effective tools to control the threats based on their intensity. These tools classify the security risks and provide visibility into threats that traditional security tools fail to discover.

This comprehensive coverage empowers your cybersecurity solution to stay vigilant, monitor potential threats, and proactively defend against malicious activities originating from the depths of the internet. Flashpoint offers organizations the ability to monitor and analyze illicit online activity, including cyber threats, fraud, and other security risks. Flashpoint’s technology enables businesses to gain insights into potential threats and vulnerabilities, helping them to better protect their assets and respond effectively to emerging threats. Our Dark Web Hunting service constantly searches the surface, deep, and dark web to identify and detect nefarious activity potentially targeting your organization. We then transform these adversarial threat patterns and activities into tailored analytical data explicitly focused on your business priorities. Our hunters identify state and non-state sponsored cyber threat actors/patterns, insider threat indicators and methodologies, as well as espionage tactics that span industries, ecosystems, and global landscapes.