A secure network can prevent cybercriminals from gaining access to your connected devices where personal information is stored. 2FA adds an extra layer of security by requiring additional verification (like a code sent to your phone) to access your accounts. It then asks you to validate if certain usernames, email addresses, and other personally identifiable information is – or have been – yours. This Accuracy Check helps the service better understand your online fingerprints so it can track it to the farthest corners of the Web. Depending on the size of your digital footprint and your online privacy setup, your personal data may be leaking in small drips or flooding onto the Dark Web. As it pools together, hackers use it to fuel other criminal operations, combining details and reusing them for subsequent attacks.
How Proactive Monitoring Can Help Reduce Company Risk
It offers a complete package that users always look for and thus emerges in the best dark web monitoring tools list. These tools classify the security risks and provide visibility into threats that traditional security tools fail to discover. When the tool detects a threat, it creates alerts and notifies the team members and everyone else within the organization so they can take action to minimize the risk. Also, they gain insights into the attacking methods and develop a cyber defense strategy. Businesses need dark web monitoring to safeguard sensitive data, protect customer trust, and mitigate the risks of identity theft, fraud, and unauthorized access.
Recorded Future Intelligence Cloud Platform

In 2017, the FBI quietly monitored the activity of Hanza, one of the most significant dark web marketplaces, before closing it. Along with DEA and the Dutch National Police, the FBI seized and deactivated another large dark web marketplace, AlphaBay. It’s one thing to be aware of monitoring apps, but another thing to realize their potential in practice. Dark web surveillance software uses scanners, crawlers, and scraper bots to browse, search, and extract data from hundreds of thousands of dark websites. This type of monitoring is the process of tracking and observing activity on the dark web. Monitoring software works by scouring the dark web for any mention of personal data, your business, or your employees’ information.
Each warning for data leaks also includes the type of information exposed and the essential steps to limit your exposure. If you choose a tool with these key features, you can better minimize company risk. WiFi networks can easily be hacked, so leveraging a virtual private network (VPN) will ensure that your internet browsing data stays safe.
Censys provides in-depth visibility into internet-connected assets, including the dark web. Monitors your identity online and in the deepest and darkest spaces to alert you of identity fraud, personal information exposure and more.24/7 real-time monitoring and alerts. ⚖️ Our threat monitoring practices align with the same intelligence frameworks used by enterprise security teams, scaled appropriately for small and medium businesses. This is where monitoring steps in and serves as a digital scanner, keeping an eye on the places most people will never see and ensuring your details don’t come up.
What Is Dark Web Monitoring? How Does It Work?
It’s a critical part of identity theft protection that allows you to address leaked data as soon as possible. ZeroFox Dark Web Monitoring is another software that aims to simplify the process of surfacing risks from the dark web. Continuous monitoring of compromised credentials, employee personal information, or sensitive corporate intellectual property is just the start for ZeroFox. Context built by analysing attack methods inform defensive measures you can take to protect your business, and alerts notify you of risk to your brands to keep you informed of emerging threats.
- These breaches require immediate attention, typically to change passwords that were exposed as plaintext or weakly hashed (for example, using MD5).
- Identity theft monitoring tools are usually designed to protect individual users rather than entire businesses.
- Any time you create an online account and secure it with a weak password, you leave yourself open to vulnerabilities.
- Knowing that a professional tool is monitoring the dark web for any signs of your personal information being compromised can provide significant peace of mind.
- With visibility into the dark web exposure of suppliers and cybercriminals targeting your third parties.
Best Dark Web Monitoring Tools For Threat Intelligence 2025

Discover how it works & how to protect a company’s information from the dark web. This multinational drug bust focused less on illegal marketplaces themselves and more on the dark web dealers profiting from them, leading to 150 arrests across 8 countries. Using advanced data fingerprinting technology, Terbium Labs ensures that clients’ information is protected without ever needing to see the data itself, maintaining privacy and compliance.
Marketing’s Shadow Twin: Cybercrime’s Use Of Legitimate Online Platforms
It acts as a powerful internet scanner, offering deep visibility into the infrastructure of networks and all the devices connected to them. Censys continuously scans the open and dark web, identifying devices, services, and potential vulnerabilities. This comprehensive scanning allows researchers to discover a massive number of compromised devices or services before they’re exploited. When the monitoring system detects a match—for example, an employee’s credentials published in a cybercriminal forum—it triggers an alert. These alerts are then forwarded to the security team to check for false positives. Once a legitimate data leak is confirmed, it passes through a remediation workflow involving securing all compromised accounts and systems before they are compromised from the exposure.
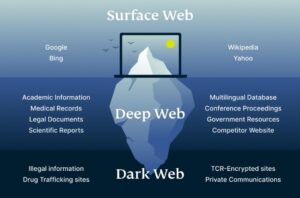
Dark Web Monitoring
Dashlane is a popular password manager, but it excels in basic password management functionalities and includes a unique dark web monitoring tool. It notifies users of any leaked passwords and encourages them to act immediately. The tool collects and analyzes thousands of database dumps and pastes the information about billions of leaked accounts. It has a Universal Search engine that automatically allows users to relate Falcon Intelligence Recon results with other CrowdStrike modules. The Express plan is best for SMBs, while the other is for mid-sized and large organizations. Moreover, you can integrate this solution into primary tools like SIEM and SOAR, making it one of the best dark web monitoring solutions.
Attackers Increasingly Using Legitimate Remote Management Tools To Hack Enterprises

A search engine designed to make it easier to discover dark web data sources and onion sites on the Tor network. It has such features as strong search and privacy protection by not storing any user data. Onion Search Land is a well known and appreciated tool to researchers when looking for forums, marketplaces, or other hidden services on the dark web with regard to scrutinizing illegal activities.
Recorded Future’s dark web monitoring equips businesses with crucial insights for protecting vital data. Exploring the intricacies of dark websites reveals a complex underworld where cyber threats and criminal forums thrive. These sites often harbor malicious software and compromised credentials, posing significant risks to individuals and organizations alike.
With Flare’s Dark Web Monitoring You Can:
- This dark web monitoring tool looks into thousands of darknet platforms, pages, and forums to provide instant access to over eight years of data.
- This process is vital for identifying compromised credentials, insider threats, and other sensitive data breaches that often occur in the shadows of the deep and dark web.
- They achieve this by fortifying IT systems, addressing vulnerabilities, and promptly notifying all relevant parties, minimizing the potential fallout from such incidents.
- It’s not filled with malicious actors looking to sell or data or steal from you.
- Dark web sites are anonymously hosted websites accessible only through special software—commonly “TOR” (The Onion Router).
Get notified of weak, reused, and old passwords with personalized recommendations and alerts. Create strong, unique, hacking-resistant passwords for new and existing accounts. AI can scan images, QR codes, and screenshots shared on the dark web to identify threats.
Your information is sensitive—it’s incredibly easy for hackers or cyber criminals to gain access to your personal or financial information with your knowledge. It’s not filled with malicious actors looking to sell or data or steal from you. For businesses, Dashlane offers features like customizable security settings (2FA, single sign-on, and more) and employee groups for secure password sharing and increased productivity. It combines dark web intelligence with geopolitical and nation-state threat detection. Yes, individuals can use tools like Have I Been Pwned or Cyble Vision for free or personal protection. For businesses, a publicized data breach can lead to loss of customer trust and long-term brand damage.