Recorded Future’s extensive threat database and predictive capabilities make it an essential tool for proactive cyber defense. Schedule a demo to discover how Kaseya 365 keeps leaked data on the dark web from leading to account corruption and unwanted consequences. Kaseya’s Business Enablement Program is structured to support MSPs in adapting to the dynamic IT landscape while delivering premier client services. Tap into expert training, marketing assistance, and business consulting to elevate your offerings and maximize revenue. Google’s free tool goes a step further, offering people a button on the results about you page to request Google remove their personal information from search results as well.
History Of Dark Web Monitor

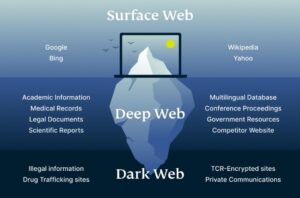
It consists of websites and resources that are openly available to users without any special access requirements or encryption protocols. The deep web includes all the pages that search engines don’t index including password-protected websites and websites that choose not to be “crawled” by search engines. The deep web contains content that’s stored in databases that support services on the clear web, such as social media platforms or subscription streaming services. SpyCloud is a renowned cybersecurity vendor that provides a good range of cybersecurity solutions to protect users against threats and cyber-attacks.

It scans the shady corners of the internet for any sign of your data, giving you a dark web monitoring alert before cybercriminals have a chance to take advantage. As many as 9% of people in the United States are the victims of some form of identity theft each year. The dark web is a secret network of websites not indexed by major search engines, and only accessible via certain browsers and software. Learn how dark web monitoring works, why it matters, and how to take proactive steps to safeguard your personal information before it falls into the wrong hands.
Financial Information
- Is a Clear Web site that performs free searches of the Deep Web and the Dark Web for personal or business information.
- Dark web monitoring is crucial as it helps businesses identify if they have any compromised sensitive data in illicit communities.
- Google Workspace accounts and supervised accounts aren’t able to use dark web report.
- Customers of the service get access to an account-protected dashboard where alerts are displayed when cyber threat intelligence related to that has been identified.
However, harnessing this intelligence requires a deep understanding of the dark web and effective investigative techniques. MyPwd uses artificial intelligence to scan the deep web and the dark web to determine if any of your personal passwords have been leaked. They’re constantly on the lookout for evidence of the sale of databases, credit cards, illegal services, or cyberattack planning. Identity Guard is owned by Aura and is one of the best identity theft protection solutions on the market today. Identity Guard uses your email address to scan the dark web for any compromised data.
But centers of illicit commerce remain on the dark web, and new ones spring up all the time. Dark Web Monitoring notifies you when your data is discovered, allowing you to respond quickly to security breaches, helping to minimize their impact. The deep web is just a secure, back-end platform where you’ll find things like document-sharing sites, your email, and other secure log-in sites. These selectors allow Intelligence X to gather open-source intelligence from places like the darknet, document sharing data, whois data, public data leaks, and more. As a search engine, Intelligence X is unique because it works with “selectors”—specific search terms such as email addresses, domains, URLs, IPs, CIDRs, BTC addresses, IPFS hashes, and more. CIH’s platform offers continuous data collection with updates every two minutes, AI-powered risk categorization, and a free-text search function for investigations.
Cyber Threat Resources
Its user-friendly interface and robust reporting capabilities enable security teams to identify and respond to threats quickly. It integrates with existing security systems, offering seamless threat intelligence and actionable insights. Dark web monitoring seeks to identify and reduce potential hazards and threats by gathering information from these anonymous online groups. Download Kaseya’s Top 10 Tips for Improving IT Security to learn the importance of dark web monitoring and explore nine additional must-have motions for developing a quality security posture. Receive real-time, actionable notices when vulnerable data is found, allowing for swift action to prevent unapproved access. This automation enhances efficiency by delivering instant insights into risks, so your team can prioritize and respond without delay.
Cobwebs Technologies Web Investigation Platform

Our dark web monitoring technology collects data from the most extensive base of sources in the industry. Fully automated collection and source-infiltration gives us the ability to scrape data that is inaccessible to other vendors, including high-value sources with complex CAPCHA and posts that have since been deleted. Because there is no published directory of sites or hierarchy of information on the dark web, finding sources to monitor requires considerable expertise. Dark web monitoring must be done covertly, to keep security teams anonymous and to avoid exposing sensitive company information. The dark web is only accessible via the Tor browser, and no complete listing of dark web sites exists. As noted above, in order to be able to visit a particular site on the dark web, you need to know its URL.
Aura Dark Web Scanner
Cyberint is an ideal partner for organizations that need a combination of cutting-edge technology and human expertise to monitor for a wide range of external risks and take rapid action. Its ability to create virtual personas and engage with threat actors gives it a unique advantage in gathering targeted intelligence and understanding the context of threats. Cyberint is particularly effective at targeted intelligence and engaging with threat actors to gather more information, often with the ability to create fake personas to gain access to exclusive communities.

Best 8 Dark Web Monitoring Tools

Dark web monitoring services scan the dark web for stolen or compromised personal and business data. Common types of leaked data include login credentials, credit card numbers, and confidential documents. These services search hidden websites, forums, and marketplaces where cybercriminals buy, sell, and trade sensitive information. If your data is detected, you receive an alert with details about the breach, allowing you to take steps to secure your accounts. Businesses use these services to protect customer data, intellectual property, and brand reputation.
As a result, Dark Web Monitor is fit for daily use and able to meet the operational requirements of agencies throughout the world. And it comes with a 60-day money back guarantee for annual plans, too.Protect your digital life. The longer you wait, the longer you expose yourself to ID fraud—or financial fraud.
What To Expect From Dark Web Monitoring Services For Businesses
However, consumers are primarily interested in the companies that work to keep their personal information safe and secure. The Dark Web is a network of websites and (often illegal) marketplaces that can’t be reached via normal search engines. (This is not to be confused with the deep web, which contains password-protected web pages, such as your email inbox or social media settings). If your information is on the dark web, it means that it has likely been compromised, stolen, or leaked by cybercriminals. This poses a significant risk to your identity, finances, and reputation, and immediate steps should be taken to mitigate further damage. Failure to act quickly can lead to identity theft, fraud, or even targeted attacks that exploit the compromised data.
The platform monitors social media platforms for threats and provides phishing detection and takedown services. It is designed to protect organizations from digital threats that can impact brand reputation and customer trust. ZeroFox is ideal for mid-market to high-end enterprises with a significant online presence and brand image concerns.
The best Dark Web scans spot protected accounts as soon as their details appear on a Dark Web forum, enabling users and account administrators to change login credentials immediately. As such, Scout is a data loss prevention system and an insider threat protector as well as a threat-protection system. When a Dark Web threat is spotted, Scout raises an alert in the monitoring dashboard.
CrowdStrike Falcon® Intelligence™ Recon is a key component of the CrowdStrike platform, offering a powerful tool for deep and dark web monitoring. Vision UI is an easy-to-use app that offers an intuitive and user-friendly interface backed up with querying solid capabilities to search, monitor, and create alerts for users’ sensitive information. The investigation begins by entering the keyword or other operator in the search bar. The Boolean and Regex-supported search logic allows deep and highly targeted queries. OpenCTI is another open-source option for collecting, managing, and interacting with intelligence data. ThreatCover offers tooling for security analysts to deep dive into threat intelligence feeds, allowing optimal data quality and context from which response teams can initiate incident response.