
Connect with a Chase Private Client Banker at your nearest Chase branch to learn about eligibility requirements and all available benefits. Invest on your own or work with an advisor — we have the products, technology and investment education, to help you grow your wealth. Morgan Wealth Management Branch or check out our latest online investing features, offers, promotions, and coupons.

Dumps – Magnetic Stripe Data
While criminals in the past might have stolen card data for their own reuse in carding, modern criminals split into those who capture and skim card data, and carders who take stolen card data and use it to make illicit purchases. Dark web monitoring platforms, such as Lunar, provide an automated solution to safeguard personal identifiable information (PII) and credit card details. These platforms continuously scour the deep and dark web, looking for any traces of your sensitive information.
Best Overall Credit Monitoring Service
Prior to joining CSO, John wrote and edited articles for PortSwigger’s The Daily Swig covering topics including web security, vulnerabilities and hacking culture. For more than 17 years, John covered a wide variety of topics including network security and enterprise technology for The Register. His work at The Register earned him a number of awards, including the BT Enigma award for contributions to technology journalism. It’s believed that the passwords were stored as SHA-1 hashes of the first 10 characters of the password converted to lowercase.
Hubble Space Telescope
Freezing your credit reports limits access to your reports and keeps creditors from checking your credit in response to a new application. As a result, creditors may deny applications in your name while a freeze is in place. You generally aren’t liable for unauthorized credit or debit purchases, but you may need to act quickly and call the financial institution to dispute the transactions. If you notice a new account was opened in your name, the company can also help you close the account. Free Dark Web scanners check a smaller portion of known hacker sites for personal information. Because these services are free, they only check for information relating to the email address you enter — this is usually limited to just leaked passwords.
Sign In Securely
This Holowear is a new rarity of Holowear which includes animations for Moves, movement, Unite Moves and more. He recommends verifying market employees carefully, and to weed out law enforcement infiltration through barium meal tests. Whilst a great many products are sold, drugs dominate the numbers of listings, with the drugs including cannabis, MDMA, modafinil,108109110 LSD, cocaine, and designer drugs.
- Enter the amount you wish to buy, and we’ll instantly calculate the BTC equivalent based on the current exchange rate.
- The resulting financial loss from stolen information is tremendous, not only for the individual victim but also for the financial provider and any involved organizations.
- Credit monitoring services scan your credit reports from one or more of the three main credit bureaus and let you know of any changes or potential fraud.
- This post examines the history and provenance of DSLRoot, one of the oldest “residential proxy” networks with origins in Russia and Eastern Europe.
What If I Think There’s A Mistake In My Credit Report?
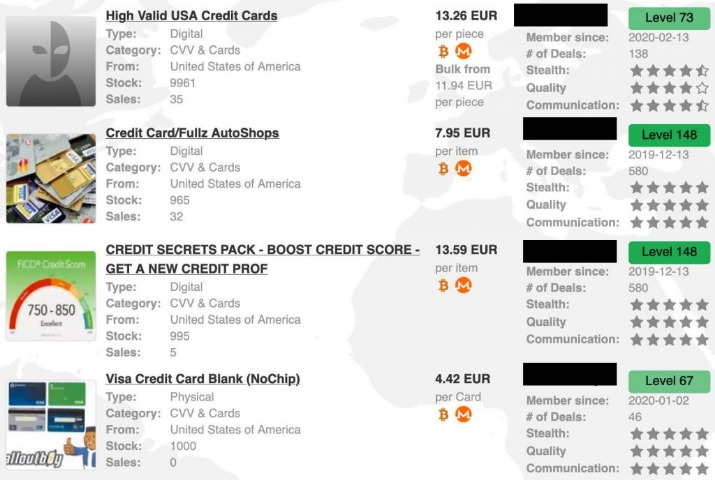
The sooner you become aware of compromised information, such as stolen credit card numbers on dark web, the faster you can take steps to mitigate damage. Rapid response can prevent unauthorized transactions, minimize financial losses, and protect your customers’ trust in your business. By leveraging dark web monitoring platforms and credit card monitoring alerts, businesses can stay one step ahead of cybercriminals, ensuring a robust defense against the ever-evolving threat of credit card fraud on the deep and dark web. Card Shops are a type of dark web marketplace that hosts the trade of credit cards and other stolen financial information.
Best Crypto Tax Software 2025 – Compare Top Tools Now
Anyone who uses credit cards for daily purchases should monitor for exposure to protect against fraudulent transactions and unauthorized access. Exposure of your credit card details can lead to fraudulent activity, which could negatively impact your credit score. Implementing a 3-D Secure ACS solution, like Outseer 3-D Secure, fortifies the fraud prevention strategy. This EMV® 3-D Secure ACS delivers a secure, frictionless digital shopping experience, providing a multi-layered defence against unauthorized transactions.
If you don’t feel safer after signing up for Aura, we offer a 60-day money-back guarantee on all annual plans — no questions asked. If you believe someone has gained access to or is abusing your personal information, contact the relevant authorities to get support — and contact any impacted companies to report your identity theft. Once your accounts and finances are secure, you can take steps to protect yourself from other types of fraud that could occur when your information is available on the Dark Web.
- It’s an ever-evolving ecosystem—constantly shifting, reinventing itself, and adapting.
- Many of those purloined tracks or “grails” he later sold or gave away on forums.
- Finally, the 6 Star EX for Molayne & Alolan Dugtrio has been unlocked We’ve updated our Pok�mon Masters Day page with the details of this month’s event.
- Granite Credit Union is not responsible for the content of that web site.
Top Strategies For Risk-Based Transaction Monitoring
The dark web is a network of websites where people can share information anonymously. Sometimes the activity there is harmless, like when journalists, law enforcement officials and whistleblowers gather and share info without revealing their identity. But it can also be a popular place for identity thieves, who can use the dark web to trade and sell your personal information.

Detecting Fraudulent Activity On Your Accounts
It’s also good practice to keep an eye on your credit report so that you can spot and report any errors or accounts someone is trying to open in your name. It’s easier for someone to steal your identity once your information is on the dark web. That’s why we monitor your personal information and alert you if we spot new activity or changes.
Patterns recommended to avoid include hiring hitmen like Dread Pirate Roberts, and sharing handles for software questions on sites like Stack Exchange. Over an eight-month period, a developer working for an affiliate marketer scraped customer data, including usernames and mobile numbers, from the Alibaba Chinese shopping website, Taobao, using crawler software that he created. It appears the developer and his employer were collecting the information for their own use and did not sell it on the black market, although both were sentenced to three years in prison. So, here it is – an up-to-date list of the 20 biggest data breaches in recent history, including details of those affected, who was responsible, and how the companies responded. There’s no way to make yourself invulnerable to credit fraud or identity theft, but there are actions you can take to mitigate the risk. Several of the services we chose also alert users if their personal information appears on the dark web, though the offerings are more limited than with paid iterations.

Financial institutions and security teams have developed pretty sophisticated detection methods that focus on behavioral patterns. Automatic payments get declined, travel plans get disrupted, and sorting everything out with the bank can take hours. When fraudulent transactions occur, merchants frequently end up eating the costs through chargebacks.
If you don’t take the proper steps to secure your credit card information, you place yourself at risk of becoming a victim of identity theft which is not easy or quick to recover from. “I’ve been able to get all-inclusive trips and holidays, and my Netflix accounts and Spotify,” D2 said. He showed off his account on Deliveroo, a British online food delivery company, where he had 65 credit cards saved. Discover the pros and cons of using credit cards or card for purchases, including benefits and risks, to make informed financial decisions. The ease of access and navigation of Telegram carding groups is a major concern, as it allows cybercriminals to easily buy and sell compromised payment card details.



