That is, assuming you know where to find the right 16-character .onion addresses. This is done typically to circumvent regulatory powers, avoid detection, or simply to obtain illicit or illegal goods. Dark web markets work in a way that is not like your everyday online shopping.
Attempting to even view these can be illegal in many countries and states, so stay well clear of them if you want to keep a clean record and conscience. Abacus Market is one of the newer darknet marketplaces that quickly filled the gap left by AlphaBay’s takedown. It hosts over 40,000 listings and offers everything from illicit goods and substances to hacking tools. With an estimated market value of around $15 million, it has grown into a massive hub for cybercriminal activity.
How To Access The Dark Web Safely And Securely
MFA requires users to provide multiple forms of verification, such as a password and a one-time code, making it more difficult for attackers to exploit stolen credentials. The connection between the dark web and cybersecurity risks is evident. A 2023 IBM report found that the average cost of a data breach exceeded $4.45 million globally, with SMEs disproportionately affected. Addressing these vulnerabilities through comprehensive cybersecurity risk assessments and cybersecurity for businesses is essential to prevent data breaches in small businesses and safeguard sensitive information.
Malware Sales
If you want to be extra safe, routing your connection through a VPN and then accessing the dark web using the Tor browser provides more security than Tor alone. You can also use the Tails operating system to further protect yourself. If you’re just browsing the dark web out of curiosity, Tor, or a Tor and VPN configuration is safe enough. If you’re trying to hide from an oppressive government or want to be a whistle-blower for something illegal, take as many steps as you can to be safe. Darknet markets operate within this hidden space, often hosting illegal activity, while the deep web primarily consists of everyday private or password-protected content. Even if you’ve never visited these markets, your personal and financial data might already be there, having been leaked through a data breach.
Top 20 Benefits Of Using Agentic AI For Businesses
Cybercriminals on the dark web marketplace always look for new victims to target them with scams or infect their devices with malware, spyware, or adware. Thus, use the best antivirus software that protects against these online threats. The Torrez market is one of the biggest dark net marketplaces, also called a community-driven marketplace. It contains a good selection of product listings that range over 35,000 items. The website has an interface and design similar to other dark web shops. It uses PGP encryption, two-factor authentication, and OPTP authentication to ensure users’ security.
Making Cybercrime Easy For Anyone
- To purchase illicit goods or services, users deposit cryptocurrency into an escrow system or directly to the seller, and the cryptocurrency is held until the buyer confirms the satisfaction of the transaction.
- Software firm Hyperion Gray put together a map showing all 6,608 dark web sites crawled during January 2018.
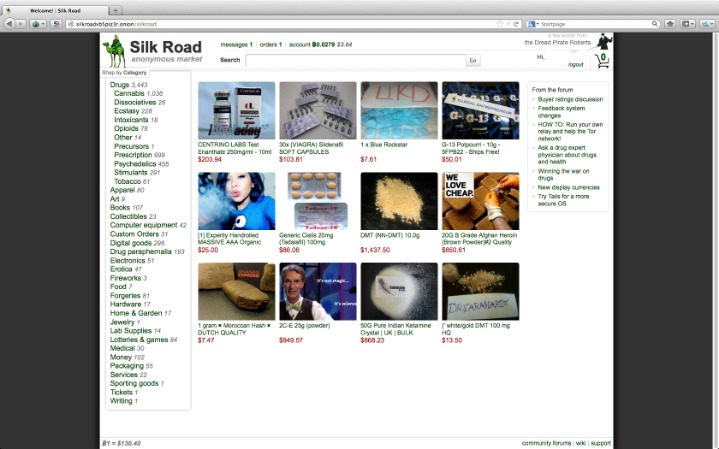
- United States President Donald Trump has pardoned Ross Ulbricht, the imprisoned founder of the dark-web black market Silk Road.
- Sometimes raids similar to these yielded information dumps not unlike the ones you would see in the news, like Hacking Team and others.
- Indeed, they must frequently be accessed by cybersecurity organizations conducting threat hunts or defending their networks or those of their clients.
- First, let me explain that this article is intended for users who want to use the dark web for legal and needed purposes, such as finding censored news, blocked websites, and other much-needed services.
Click on “Safest.” As you’ll see, JavaScript and a few other features will be automatically disabled on all sites. However, if you must buy items from the dark web, set up a secure, encrypted email with CounterMail or ProtonMail. For more information, read more about the most secure email service providers in my other post. Now that you’ve completed the download, it’s time to install the Tor browser on your device. (The installation instructions that follow are for the macOS platform, I’ll mention where it’s different for Windows.) Simply double-click the downloaded file in your download folder.
Early Warning Signals For Predicting Cryptomarket Vendor Success Using Dark Net Forum Networks
Then, simply click the operating system that you are using and download the file. While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store. It’s impossible to access the dark web with a regular browser like Chrome or Safari. That means that when Tor is compromised, or perhaps there’s a new vulnerability exploit in the Tor network, a VPN will still protect your privacy. The compromised Tor exploit might trace back to you, but then again, your VPN will lead it somewhere else – which makes it impossible to be traced back to you.
When you’re done surfing or shopping on the dark web, don’t forget to shut down Tails. The major advantage of using a live OS such as Tails is that, on shut down, the OS wipes itself from the thumb drive you’ve installed it. Well, there’s a reason why it’s recommended to browse with a minimized or rescaled window – you can be tracked based on your active window’s dimensions (yeah, they really can do that). So, do yourself a favor and rescale that Tor window as much as you can before proceeding. In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web.
Unlike other search engines, it does not collect or share web activities and personal data of users. To protect against the threats posed by the dark web, businesses must adopt a proactive and multi-layered cybersecurity strategy. These measures are essential for safeguarding sensitive data, maintaining regulatory compliance, and mitigating risks effectively. SMEs often struggle with limited budgets for cybersecurity, leaving critical vulnerabilities unaddressed. Investing in the best cyber security for small business solutions, such as regular risk assessments, endpoint protection, and dark web monitoring, can provide a strong defense against these threats.
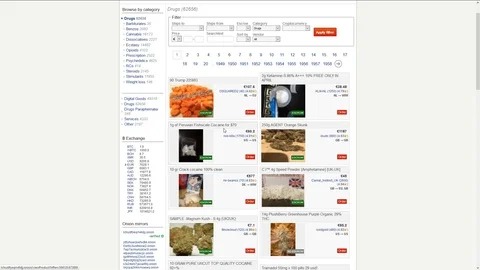
Products And Their Prices On Black Market
While it might appear tempting to venture into the dark web, it’s crucial to understand that the risks here are far more severe compared to the deep web. Therefore, if you do decide to explore it, exercise extreme caution. There are often copious amounts of how-to articles, software exploits, and hacked credentials for sale. Not every visitor is a criminal, but this is where most cybercrimes begin. No user names are tied to actual identities, and no moderation like one may find on Reddit. Users leverage these platforms to organize protests, whistleblow, share survival guides, or share files P2P.
Fraud And Hacking Services
- It’s somewhere Google and Bing don’t index, and you need special tools to get to it.
- At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen.
- There are three ways to reach and explore the dark web’s black markets.
- Some services are genuine; you can get what you want at an agreed fee.
- Take a look at the sites that these directories have collected and see what topics interest you.
While it hosts legitimate uses, such as protecting privacy in oppressive regimes, it is also infamous for facilitating illegal trade in drugs, weapons, counterfeit documents, and stolen corporate data. Cybercriminals go on dark web marketplaces to buy and sell illicit goods and services. They engage in financial crime and sell other people’s stolen personal information, since they’re under the veil of anonymity. Still, even with these crackdowns and better defenses, dark web markets just keep coming back.


However, VeePN does not advise you to even attempt to access the black market via any device because of the high risks. Also, check how to know if someone is spying on your phone to stay protected from intruders and surveillance. If you browse black market just for fun and occasionally register to this marketplace without essential privacy protection, hackers can steal way more than just your login credentials and credit card numbers.
Search Darknet
If you’re lucky enough, you can find it on clearnet privacy forums. At Cybernod, we specialize in providing cybersecurity services for businesses, designed to protect SMEs from the ever-evolving cyber landscape. Whether you need assistance with dark web monitoring, compliance with data protection regulations, or advice on selecting the best cybersecurity solution for small businesses, our team is here to help.
Therefore, it’s likely that not all deep- and dark-web file repositories represent good intentions. Accessing and using Dark Web protocols such as Tor is not illegal; it’s just been adopted as the platform of choice by many bad actors who undertake illegal activities. Norton VPN fortifies your internet connection with ultra-secure AES-256 encryption, masks your IP, and never logs your activity. And, with an automatic kill switch that guards against unexpected exposure if the connection drops, you can enjoy powerful privacy protection as you navigate even the darker corners of the web. The dark net’s layered encryption and routing protocols offer stronger anonymity, making onion sites appealing to whistleblowers, political dissidents, privacy advocates — and, inevitably, cybercriminals.



