Using TAILS is yet another security measure that protects your online identity on the dark web. It...
wpadmin
Now that we’ve learned how to use the best dark web websites to find useful and interesting...
If you’re curious about how to explore .onion sites safely and effectively, this guide will walk you...
Now you know a little bit about DarkFox Market and what advantages it has. Keep in mind...
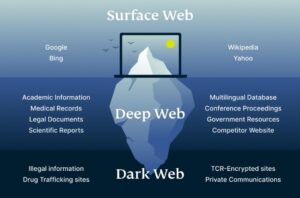
Contrary to its notorious reputation, the dark web is not just a hub for illicit activities but...
In this situation, you might be advised to take a combination of the 1-mg and 2-mg tablets...
It supports Bitcoin and other cryptocurrencies, ensuring safe transactions between parties. Escrow has handled thousands of trades,...
For example, I strongly advise using a reliable VPN like NordVPN. Although the Tor browser has sufficient...
We review and list tools and products without bias, regardless of potential commissions. Radar Rundown Free firewall...