To turn it on, just go to the “Settings” and then the “Tools” section of the NordVPN app and activate “Dark Web Monitoring.” In the end, it’s all about staying one step ahead. The more proactive you are, the better you can protect yourself against identity theft and other cyber threats. And, of course, think twice before sharing too much personal details online.
News Updates

If you ever have to connect to public Wi-Fi, make sure to use a VPN to keep your browsing safe and private. These days, dark web forum admins are stepping up their game. They’re tightening security and carefully screening anyone who wants to join. This vetting process helps keep the community “clean” from spies, law enforcement, or anyone who might pose a risk. However, the dark web is so complex and vast that if law enforcement takes down one market, it pops up elsewhere. For instance, after the closure of Genesis Market, its website came back after a few weeks.
Does Silk Road Still Exist?
I leave it entirely to you to decide what you think it means. By the time I’d finished my work in 2010, the world seemed to be different. There are photographs of people I recognize—prominent politicians, mostly—and, next to each, an amount of money. The site’s creator, who uses the pseudonym Kuwabatake Sanjuro, thinks that if you could pay to have someone murdered with no chance—I mean absolutely zero chance—of being caught, you would.

Major Darknet Reseller Arrested In France With 30 Kilos Of Drugs & €190k In Cash Seized
They engage in financial crime and sell other people’s stolen personal information, since they’re under the veil of anonymity. Wondering if there’s an OG darknet market for financial crimes? The market facilitates trades in stolen credit card data, hacked bank accounts, and services to facilitate the laundering of cryptocurrency.
The Top 10 Darknet Marketplaces Of 2025
If you’re after a darknet market with variety and a forward-thinking edge, Tor2door Market’s a contender—watch it close in 2025 as that AI kicks in. The Assassination Market can’t be found with a Google search. It sits on a hidden, encrypted part of the internet that, until recently, could only be accessed with a browser called The Onion Router, or Tor. To put it simply, Tor works by repeatedly encrypting computer activity and routing it via several network nodes, or “onion routers,” in so doing concealing the origin, destination, and content of the activity.
This ‘invisible’ Data Trail Can Reveal Your Location To Scammers
- Track and analyze darknet activities using our advanced cyber threat intelligence platform to stay ahead of emerging threats.
- Purchases through links on our pages may yield affiliate revenue for us.
- Anyway, this was a huge discovery for Chris, to be able to read any message on the site that other users were sending to the administrator.
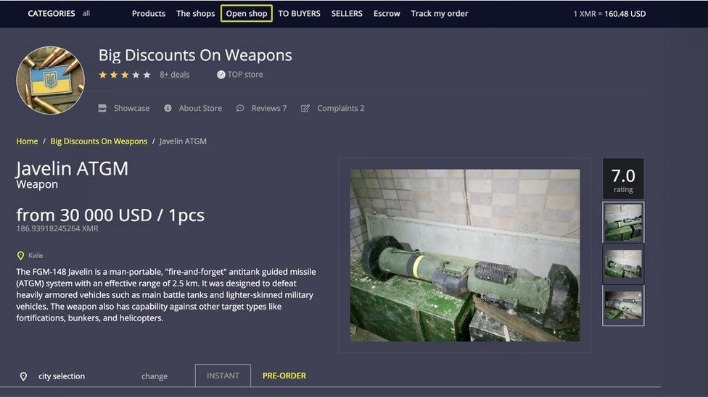
- Valued at approximately $15 million, Abacus Market is one of the most lucrative platforms in the dark web ecosystem.
- It is used by many for buying or selling items that are prohibited on the regular internet, like fake IDs, illegal drugs, and stolen data.
Our team searched the dark web and put together a list of the most active dark web marketplaces in order to assist you in monitoring illegal trade of products, cybercrime activity, and dark web trends in the dark web space. Many people go to the dark web to buy things they can’t find elsewhere, but what if what you’re buying is also trying to harm you? Scammers on darknet markets claim to offer legit tools or services, but instead provide you with malicious software that can infect your device. Some vendors offer services to help people “clean” illegally obtained funds using cryptocurrency and fake transactions. They mix and transfer funds through various privacy wallets and escrow services to hide the original source and make the illicit transactions harder to trace.

The Dark Web: A Breeding Ground For Illicit Activities
We’re back with another video in our Webz Insider video series on everything web data. Any drug marketed as an opiate, be it pressed pills or heroin, may also contain amounts of tranquilizers or fentanyl. Note that loading sites with TOR usually takes considerably longer than on the clearnet.
He was also inspired by his favorite book, Alongside Night — about a society built upon an open marketplace — to create what would become the Silk Road anonymous market. The possibility of crowdfunded assassinations underscores the importance of ethical considerations in technological advancements. While these cases remain largely hypothetical, they underscore the need for vigilance, robust regulatory frameworks, and continuous dialogue about the ethical use of digital platforms. Cryptocurrencies like Bitcoin, known for their decentralized nature and anonymity, are often used in the Darknet’s illicit transactions. In the alleged assassination crowdfunding instances, they could potentially be used to ensure donors’ anonymity and facilitate transactions. One of the biggest problems cybersecurity teams face isn’t a lack of tools — it’s too many alerts.

Thanks to the take of the final Heist (The Big Score) of the story mode, you can gather up to $40,000,000 for each of the three protagonists, which you can then invest in the stock market and turn into billions. All assassination missions are marked with a green “L” on the map. I slowly began to realise that Chris’ story was far from unusual. Again and again, I saw the same echoes of Chris in what was happening everywhere. The way power worked was changing as quickly as the technology that it flowed through.
What Is A Cloud Access Security Broker?
- If you fall for it and log in, they immediately steal your credentials and either sell or use them for other scams.
- It also runs on the Tor network, which helps keep things anonymous.
- Others sell pirated eBooks, academic materials, and entire premium courses ripped straight from paid platforms.
- That attracted the attention of politicians like US Senator Chuck Schumer, and federal agents were put on the case.
- The Abacus Market links to the new dark web marketplace sections and took over much of the vacuum left by the AlphaBay takedown.
Now, that is not to say illegal behavior is completely beyond detection. The dark web combines encryption, anonymity, and hidden doorways to provide the perfect sanctuary for such illicit activity compared to the usual internet, which is more vulnerable and trackable. Now that you understand what the dark web is all about, you might wonder why other people do things on it. Darknet marketplaces like to exist on the dark web because it offers a service that the regular internet, or more accurately, the “surface web,” does not.
About the use of data to understand everything from our political to our commercial preferences. When one goes down, two more emerge with new ideas, better technology, and greater difficulty to track. It’s an ever-evolving ecosystem—constantly shifting, reinventing itself, and adapting. Some fake sellers take your crypto and never ship what you ordered, or phishing sites that look like real marketplaces but steal your login info. And then there’s malware—click the wrong link or download the wrong file, and your device could get infected.
Personal Information
The Pentagon hoped to create an “Arpanet” of linked computers to help top American academics share data sets and valuable computer space. In 1969, the first networked connection was made between two computers in California. In Grand Theft Auto V, the player has the ability to buy and sell stock on the two Stock Exchange websites available in-game, BAWSAQ and LCN-Exchange. Lester Crest has great knowledge of the stock market and knows how to force stock prices to increase or decrease for his own good – to buy at a low price and sell at a high price. But in his flat, with six screens in front of him, Chris plunges into the darkest and most dangerous places that exist on the internet.



