As cybersecurity improves in certain areas, the market adapts, creating variable pricing across regions and data types. These stolen cards have value because they can be used to purchase high-value items or gift cards, which can then be resold for cash. And all payments stakeholders can visit Visa’s website to see public reports and press releases regarding malware, indicators of compromise, mitigation, and protection. Once stolen card data hits the dark web, it can be hard to track down just where it lands, and it can be even harder to prosecute offenders. LeakBase, which has an important place for database leaks, emerged in 2023.
Protecting Yourself From Credit Card Fraud On The Dark Web

Protecting personal information and ensuring online security should always be a top priority. Monitoring the activity on these platforms is crucial for fraud detection, brand protection, and financial intelligence. Because of the level of anonymity, these sites allow cybercriminals, it is critical to use powerful dark web monitoring tools, such as Webz.io’ Lunar, to track emerging financial and reputational threats. This is how the site admins encourage users to post their stolen credit card details on their site first. Telegram offers near-indestructible anonymity to cybercriminals by giving them the power to create accounts that are not linked to valid phone numbers or identities.
What Are Stolen Credit Cards Used For?
Ransomware leak sites are publicity sites where ransomware groups share the details of their latest victims. However, they also play an important role in how these groups orchestrate and monetize their attacks. These sites provide the ransomware operators with a platform to accept payments from the victims, a space to shame them and apply pressure, and somewhere to leak their data if they don’t pay. In this article, we delve into the dark side of credit cards and their entanglement with the sinister world of the Dark Web, shedding light on the dangers that lurk beneath the shimmering façade of convenience and ease.
The Alarming Truth Behind Data Breaches
These bundles of personal info are called “fullz“, short for “full credentials.” So instead of looking at the prices of SSNs on their own, Comparitech researchers analyzed the prices of fullz. They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails. There’s also a privacy angle—some users live in countries with censorship or surveillance, and the dark web gives them a space to communicate or access information more freely.
All of this has made it one of the most reliable markets still active in 2025. There are a variety of illegal activities that take place on telegram channels including the sharing or sale of stolen data (credit cards, banking information, stolen credentials, etc.). While this list is not comprehensive, it is a short overview of the types of activity you might see on Telegram. The dark web has become a notorious hub for illegal activities, and credit card fraud is no exception. Criminals exploit the anonymity and encryption features of the dark web to buy and sell stolen credit card information. This underground marketplace offers a range of stolen credit card details, including card numbers, CVV codes, and even full personal information.
- The repercussions of dark web credit card marketplaces, including the rise and fall of Joker’s Stash, extend beyond monetary losses.
- The forum focuses on database leaks and includes a community that challenges the Breach forum.
- According to Elliptic, a company that offers risk solutions for cryptoassets, the unknown UniCC administrators have made an estimated $358M USD in cryptocurrency for selling stolen credit card details.
- Just in the last 3 months millions of unique credit card credentials have circulated across the deep and dark web.
- Encrypted communication channels on the dark web allow users to message back and forth in an anonymous online environment.
Protective Measures And Precautions
The real difference lies in what you can post and the poster’s anonymity. Unlike clear web forums, forums on the dark web are almost entirely anonymous and unregulated. Here, you can exchange ideas, ask questions, connect with like-minded people through social networking, or share documents and media via peer-to-peer (P2P) file sharing. There are currently several online darknet markets, but they tend to be incredibly volatile due to government intervention. If you do need to access a dark web website for legitimate reasons, you can check directories like The Hidden Wiki to help find options. The Tor network provides powerful tools for enhancing online privacy and anonymity, but these benefits come with certain trade-offs.
Cybersecurity News
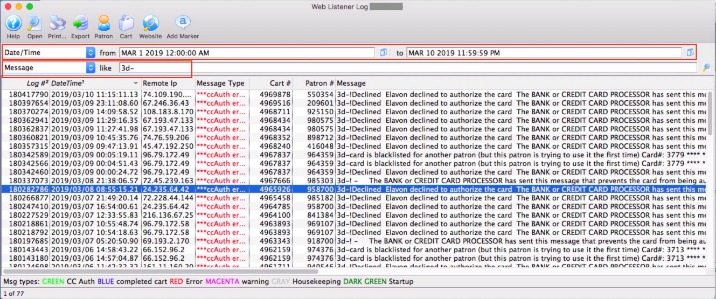
PatrickStash has two categories, Cards and Cards NoVBV (short for Verified By Visa). The site’s forum representative is very active in advertising the shop, touting automatic refunds, live statistics, and sellers in a range of countries as their USPs. From the data D3Labs has examined so far, about 30% appear to be fresh, so if this applies roughly to the entire dump, at least 350,000 cards would still be valid. Dark web posts and offers of this size are usually scams, so the massive dump of cards could easily be fake data or recycled data from old dumps repackaged under a new name.
300,000 Credit And Debit Cards Leaked On Dark Web As Hackers Infect Millions Of Devices, Drain Bank Accounts: Report
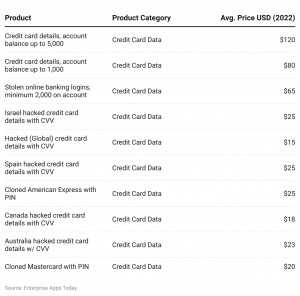
This latest pack is the fourth credit card dump the carding market has released for free since October 2022, with the previous leaks counting 1.22 million, 2 million, and 230,000 cards. As with credit cards, the location of the victim whose information is up for sale has a significant influence on price. Japan, the UAE, and Europe have the most expensive identities at an average of $25. Due to limited data on credit cards from other countries, we were unable to adequately compare prices for credit cards from different places. STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity.
Then, try LifeLock free for 30 days to help find out if your personal data is leaked on the dark web. The cybersecurity firm says the infostealer malware known as Redline was the most prevalent of the data-thieving malware, accounting for 34% of the total infections in 2024. Risepro, which primarily focuses on stealing banking card details and passwords, is another fast-spreading infostealer.
- The detailed nature of medical records allows for more complex fraudulent schemes, increasing their price and demand.
- UniCC has been active since 2013 with tens of thousands of new stolen credit cards listed for sale on the market each day.
- Interestingly, a major part of the carding ecosystem revolves around education.
- STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity.
- While the allure of cheap credit card details and the potential for financial gain may be tempting, the risks and consequences of engaging in such activities cannot be ignored.
Carefully vet the websites and online platforms you use for purchases and ensure they have secure payment methods, such as encrypted connections and two-factor authentication. Look for reputable sellers with positive reviews and avoid suspicious websites or deals that seem too good to be true. To protect yourself, it’s crucial to monitor your credit regularly, report any suspicious transactions promptly, and use secure payment methods online. Additionally, securing personal information and maintaining cautious online behavior can minimize the risk of falling prey to credit card fraud on the dark web. Launched in 2023, STYX focuses on financial crime, providing stolen credit card data, hacked bank accounts and access to various cryptocurrency laundering tools. Financial institutions can proactively strengthen their defences by integrating intelligence derived from FraudAction.
Credit cards and the dark web pose a significant threat to individuals and their financial security. The dark web serves as a marketplace where stolen credit card information is bought and sold, fueling illegal activities. Cybercriminals exploit vulnerabilities in payment systems, compromising credit card details. Once obtained, this information is used for identity theft, fraudulent purchases, and money laundering.
The Top 9 Dark Web Telegram Chat Groups And Channels In 2025
For instance, BidenCash saw a surge in user activity following its free data leaks. Social Security numbers and other national ID numbers are for sale on the dark web but aren’t particularly useful to cybercriminals on their own. A fair number of vendors include access to a SOCKS5 internet proxy that can be used by the buyer to match their computer’s IP address location with that of the cardholder in order to avoid being blacklisted. That merchant specifically mentioned that using a stolen card on a store that uses Verified by Visa (VBV) will likely void the card. Verified by Visa is a service that prompts the cardholder for a one-time password whenever their card is used at participating stores. The average price of a cloned, physical card is $171, or 5.75 cents per dollar of credit limit.



