
Likewise, some websites allow Tor, but with frequent Captchas that can be annoying. You can use a VPN if you’re in a country that restricts or heavily monitors Tor usage. You can also use it if you don’t want your network administrator or ISP to be aware of your Tor usage. However, if you don’t fall into these categories, or are a high-risk internet user (e.g., an investigative journalist or whistleblower), combining a VPN with Tor might be unnecessary. To make things simpler, HTTP stands for Hyper Text Transfer Protocol, and this protocol governs communication on the world wide web.
The best thing to do is get your hands on some good darknet directories to find secure pages regarding the stuff you want to search for. The dark web itself has a lot of dark web site directories to help you point out where you need to go. When accessing the dark web, the last thing you want is to leave traces behind that could be traced to you.
VPNs That Work With The Darknet

If you exercise due caution and use a combination of the Tor browser and common sense in which sites you access on the dark web, yes, the dark web is safe to use. You may be targeted by law enforcement, exploited by hackers, or threatened by criminals using the dark web for nefarious purposes. Tor’s anonymity has spurred many malicious actors to host dangerous sites on the network, including scams, phishing links, malware, and illegal content. The Tor browser provides access to “.onion” websites, which are Tor hidden services that you can only access through the Tor browser. You can access these websites without worrying about someone snooping on a Tor exit node, offering more private browsing of what is known as the deep web. The Tor Browser is an open-source web browser created for anonymous browsing and to evade censorship.
However, this does not provide any extra security for your device or information. There are a few reasons why the dark web isn’t stopped or shut down. First, it’s difficult to track and monitor activity on the dark web since much of it is encrypted. As such, you should exercise caution when accessing any unofficial dark websites. One of the great things about Tor is that it can be used to access both the dark and surface web. Just note that although you’ll be anonymous, you won’t have the speed or convenience of a direct connection, and some sites might block you outright.
Plan Ahead Before Connecting
Change your passwords and watch out for suspicious activity on your credit reports. Your information might be on the dark web if it was exposed in a data breach, sold, or stolen by hackers. To check, you can use dark web scanning or breach detection tools like Avast Hack Check or LifeLock Breach Detection to search for compromised data. If found, take immediate steps to secure your accounts and personal information.
- The biggest differentiator between the deep and dark web is that dark web activity is made anonymous through a variety of encryption and routing techniques.
- If your device is unprotected, you could be a victim of malware or a hacking attack.
- Once you are certain that you have the correct URL, save it in an encrypted note—the Tor browser will not cache it for later.
- You can now safely browse dark web websites and hidden wikis, but if you plan to do anything more than that, you’ll need to take several precautions.
- In 2002, the dark web grew significantly when researchers supported by the US Naval Research Laboratory built and released the Tor network.
How To Get On The Dark Web Safely (Extensive Tutorial)
These forums look similar to those found on the clear web, but the content discussed and shared by the anonymous chatters can evade censorship on public sites and surveillance. The problem is that getting to those forums may require opening yourself up to safety concerns like the ones listed above. Remember to uninstall any plug-ins you have before downloading, or prepare for them to be blocked – they can sometimes reveal your IP address, even if you’re using a VPN or onion router. Importantly, each node is representative of an additional layer of encryption.
By downloading and installing the Tor browser, you can access dark web websites securely. To access the dark web safely, you’ll need to use the Tor browser. The dark web requires special tools like the Tor browser to access its websites. The dark web is used by individuals seeking anonymity and privacy.
Dangerous And Disturbing Services And Items
Otherwise, you risk downloading fake apps that might infect your device with malware. The Tor browser is mostly used to surf the dark web or evade censorship. It’s also useful if you’re a journalist, whistleblower, or activist that needs to share sensitive data with their sources, or if you’re an undercover agent. You can also use Tor to enjoy better privacy online, but I honestly think a VPN is better suited for that. If you want to surf .onion sites, see our list of the best dark web sites in 2025.
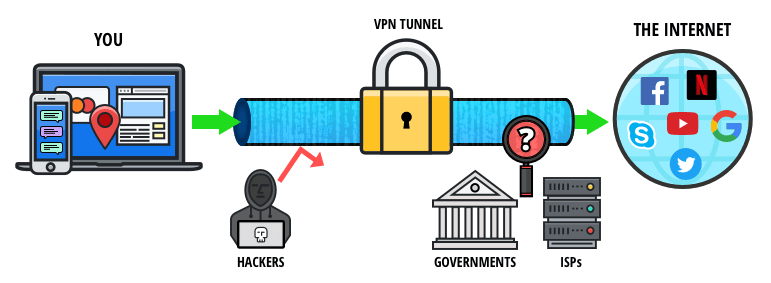
Tor Over VPN (Recommended)
Social networks, such as Facebook, have created dark web versions of their sites to address privacy problems related to their surface web versions. ExpressVPN had created a .onion version of its website to allow greater privacy and anonymity for Tor browser users. The invisible web is made up of data and information that is not indexed and cannot be searched for by using traditional search engines. It includes media and archives which cannot be crawled and indexed with current search engine technology. Like I2P, Freenet is a self-contained network within the network that can’t be used to access sites on the public web. It can only be used to access the content uploaded to the Freenet, which is a peer-to-peer distributed data store.
Download And Install The Tor Browser
Otherwise, there’s a good chance of falling victim to a phishing scam like this fake Bitcoin mixer. When using a VPN for the dark web, your ISP will not be able to see that you are connected to a Tor node, only an encrypted tunnel to a VPN server. Based on Firefox, the Tor Browser lets you surf the clear and dark web. Ensure you download the Tor Browser from the official website to avoid downloading malware, spyware, or other viruses to your device. As long as users take the necessary precautions, no one knows who anyone else is in the real world.
- Unlike Tor, I2P is designed for peer-to-peer services like file sharing, email, forums, and even decentralized websites — all within its own closed network.
- It’s somewhere Google and Bing don’t index, and you need special tools to get to it.
- This extra layer of security can deter potential hackers from gaining unauthorized access to sensitive data.
- With all this data, your ISP could create a very accurate profile of you and link it to your IP address.
- However, if you’re looking to trade or buy something, the risk of scams increases exponentially.
Understand Legal Risks
Again, they can use various tools and technologies for this, like tracking tools or social engineering techniques. This is another reason it’s best to use a VPN and be careful on the dark web to preserve anonymity. If you’re in the U.S., you can make use of helpful tools like ExpressVPN’s Identity Defender to inform you if and when any of your data ends up on the dark web. This will allow you to take action right away and reduce the risk of any further damage to your data or identity. Let’s look at two popular browsers you can use to access the dark web on desktop computers and laptops.

A VPN adds protection before Tor, closing these gaps without breaking access to .onion sites. Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for. Some of these sites can be found through regular web browsers, but you’ll then need to switch over to Tor once you’ve got the onion links you want to follow. Darknet browsers provide access to the dark web and allow for anonymous browsing. These browsers allow underrepresented groups to enjoy their right to free expression, but they also carry the risk of cybercrime.
Yes, many organizations monitor the dark web for cybersecurity intelligence—always in line with legal compliance. Analytics Insight is an award-winning tech news publication that delivers in-depth insights into the major technology trends that impact the markets. The content produced on this website is for educational purposes only and does not constitute investment advice or recommendation. Always conduct your own research or check with certified experts before investing, and be prepared for potential losses. Opinions expressed herein are those of the authors and not necessarily those of Analytics Insight, or any of its affiliates, officers or directors.
How Do I Access The Dark Web Safely Using Tor Browser?
Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online. Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine.



