
Once you’ve securely connected to the Dark Web via Tor, the next step is locating legitimate .onion sites. Unlike traditional websites, .onion addresses aren’t indexed by mainstream search engines, requiring specialized methods to find them safely and reliably. The Tor Browser is an open-source web browser created for anonymous browsing and to evade censorship. It routes users’ traffic through thousands of volunteer-run servers called nodes/relays. These nodes/relays and the websites operating on them make up the Tor network, or as it is more generally named, the dark web.
Top VPN Deals
The dark web is a part of the internet that isn’t indexed by search engines. You’ve no doubt heard talk of the “dark web” as a hotbed of criminal activity — and it is. Researchers Daniel Moore and Thomas Rid of King’s College in London classified the contents of 2,723 live dark web sites over a five-week period in 2015 and found that 57% host illicit material. Whited’s rule of thumb is to use the Tor Browser instead of Private Browsing Mode or Incognito Mode. “Contrary to what most people think, these modes do not actually protect your privacy,” she says.
BBC Tor Mirror
Law enforcement agencies keep an ear to the ground on the dark web looking for stolen data from recent security breaches that might lead to a trail to the perpetrators. Many mainstream media organizations monitor whistleblower sites looking for news. Dark web commerce sites have the same features as any e-retail operation, including ratings/reviews, shopping carts and forums, but there are important differences. When both buyers and sellers are anonymous, the credibility of any ratings system is dubious. These groups develop their own sophisticated malware, sometimes combined with pre-existing tools, and distribute them through “affiliates”. The dark web is a subset of the deep web that is intentionally hidden, requiring a specific browser—Tor—to access, as explained below.
Can Malware Be Present On The Dark Web?
You can find sites like Facebook, Wikipedia, e-commerce sites, YouTube, and more here. No, as the Tor network is not good for torrenting — some Tor browsers block P2P traffic, and even Tor’s developers ask users not to use the network for P2P downloads. That’s because Tor’s speeds are pretty slow and its bandwidth is limited, so torrenting over Tor will cause even more slowdowns. Plus, I don’t think that torrenting over Tor is secure, as some Tor servers can see your IP address, which is terrible for your privacy. Tor’s speeds are really slow because it encrypts your traffic multiple times. Each layer of encryption increases the time it takes for data to travel between your device, Tor’s servers, and the sites you visit.

Dark Web Tools And Services
Neither ZDNET nor the author are compensated for these independent reviews. Indeed, we follow strict guidelines that ensure our editorial content is never influenced by advertisers. Launch the Tor Browser from your desktop or Start menu, then click Connect on the welcome screen to establish a secure connection to the Tor network.
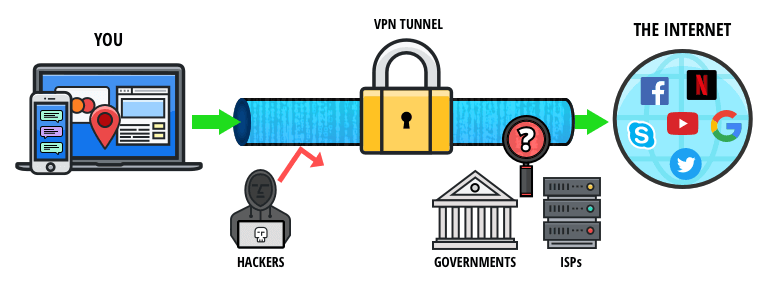
Why Use The Tor Browser With A VPN
The button above leads you to its website where you can claim an exclusive 70% discount for the 2-year plan. Click the button, get the provider for around $3.3/mo, and install it on your device. NordVPN works on every Tor-friendly system – Windows, Android, Linux, and macOS. On top of that, Tor’s nodes can also malfunction because they’re owned by volunteers, which will expose your traffic and sensitive information.
How To Get On The Dark Web Using Tor Browser
With your VPN active and Tor installed, you’re now ready to connect. Microsoft Word is one of the best word processors around, allowing you to craft powerful documents with an intuitive interface. If you know how to use Microsoft Word, you’re typically working with large files that span multiple pages. So, you’ll be happy to know there are several easy ways to delete a page in Word, including both blank pages and those you simply no longer need. Dark web marketplaces offer a range of both legal and illicit goods. Here’s a look at several of the illegal items you can buy — with prices — courtesy of Privacy Affairs’s Dark Web Price Index 2023.
They exchange sensitive information and data and, at times, have to risk their lives or that of their informant if they don’t share data under the safety of the deep web. Information on the dark web is not meant for public consumption, and the dark web protects personal data intended to be private. Law enforcement agencies frequently target sites that distribute child pornography.
This traffic is transmitted in a single direction through the network, making tracking almost impossible. The Tor Project also offers the Tails operating system for users who prefer a complete privacy solution for accessing the dark web safely. DuckDuckGo offers an .onion version of its search engine, while Sci-Hub offers access to millions of scientific articles and papers.
- Malicious actors and government agencies can run Tor nodes, compromising privacy and security.
- This simple habit can prevent many potential security issues and help you avoid getting hacked.
- The dark web is a decentralized web, which means that the data is stored on many different servers around the world.
- Talking about copycats and potential risks, due to its high risk and low signal-to-noise ratio for legitimate content, we advise beginners and privacy-conscious users to avoid The Hidden Wiki.
- The dark web is like the mysterious basement of the internet — dimly lit, a little spooky and filled with stuff you probably shouldn’t touch.
- It can only be used to access the content uploaded to the Freenet, which is a peer-to-peer distributed data store.
Pirate Bay, a BitTorrent site that law enforcement officials have repeatedly shut down, is alive and well there. When you use the Tor network, your traffic is layered in encryption and routed via a random relay, where it’s wrapped in another layer of encryption. For the utmost privacy and security, combine Tor with a VPN connection. This encrypts your online traffic before entering the Tor network and shields your actual IP address.
Navigating the dark web responsibly and cautiously will help ensure your experience remains secure. Always prioritize safety and legality, and remember that your actions on the dark web can have real-world consequences. The landscape of the dark web (and cyberthreats in general) is constantly changing, with new threats emerging regularly. Keep yourself informed about the latest security tips and potential risks by following cybersecurity blogs or forums. Keeping your security software up-to-date is vital in protecting your device from threats. Regular updates ensure your antivirus and firewall can detect and block the latest malware.
You don’t need special tools or a dark net browser to access most of the deep web; you just need to know where to look. Specialized search engines, directories, and wikis can help users locate the data they’re looking for. You can now safely browse dark web websites and hidden wikis, but if you plan to do anything more than that, you’ll need to take several precautions. If you plan to purchase on a dark net marketplace or dark web commerce sites, you’ll need to create a fake identity. Remember only to make purchases using digital currencies and never provide any online banking login details.



