You could be monitored closely even if you are not doing anything illegal. Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people. Moreover, malicious actors can attempt phishing scams to steal your data and identity for extortion. If the above average Joe’s explanation isn’t enough for you, below are some legitimate reasons to use the Dark Web in a bit more detail.
- Since Verizon acquired the company in 2017, the spokeswoman said, its practice was not to alert users of police requests for data.
- The 23-year-old had previously been identified after law enforcement discovered Welcome to Video hadn’t concealed its server’s IP address, which they later learned was registered in his name.
- And encryption-protected criminals proliferate information that streamlines minor online exploitation.
- One genuine exception is a site called Keybase, which helps you securely share files and chat online.
- Also, you can set a strong password to protect your message and choose how long it will take to expire.
- I thought it was just part of the government’s narrative to turn people against him, because he had this cult-like following.
Construction Workers Stumble Upon A Headless Female Torso In The Woods
Some of these sites are very helpful (but unseen as Google doesn’t show them), while others are just for fun. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms. Having established inter-rater reliability, the remaining case material was coded by the second author.
Child Abuse On The Dark Web
In 2020, the IWF said analysts actioned 68,000 reports which were tagged as including “self-generated” child sexual abuse content – a 77% increase on the previous year. Some tools, like Stable Diffusion, seemingly rely on open source tools that can make images generated by the tool harder to track and police online, the Post reported. Stability AI, which created Stable Diffusion, doesn’t record all Stable Diffusion images like other AI tools like Midjourney and DALL-E do, The Post reported. There seems to be no precedent, however, as officials could not cite a single prior case resulting in federal charges, the Post reported.
Enjoy More Secure Browsing With A VPN
Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy. Keybase is a fantastic onion website that lets you cryptographically bring your different online identities together. It has a feature called CoinJoin that combines multiple coins from different users into a single transaction.
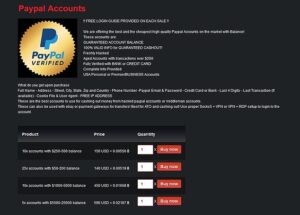
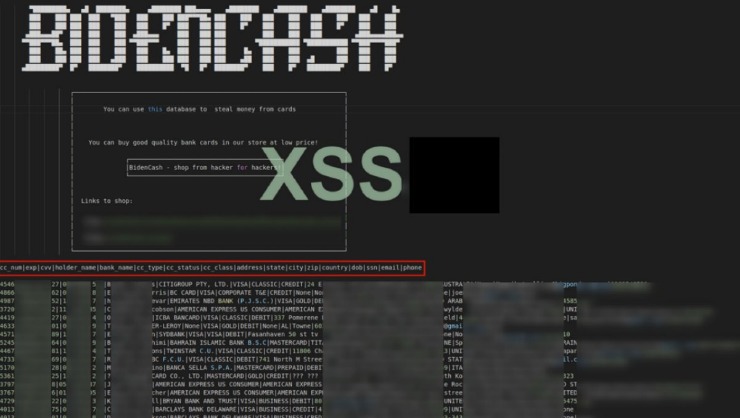
Visitors to those sites are now greeted with a message from law enforcement saying the domain has been seized. So, that can run the spectrum—from credit card fraud to sextortion to child exploitation material,” explained Secret Service Supervisory Criminal Investigator Ken Henderson. Once you’re in, though, you also find an online marketplace filled with offers for many illegal goods and services.

PSA: Don’t Use This Fake Wasabi Wallet To ‘store’ Your Bitcoin
A total of 36 countries, including Britain, joined forces to dismantle the platform. In March, police conducted coordinated raids across 31 nations in what Europol’s Guido Limmer described as the “largest operation ever” of its kind. This January, the FBI was part of another international operation that took down the cybercrime marketplaces known as “Cracked” and “Nulled”.
Latest Videos

A reliable, fast, and user-friendly VPN service offering lots of customizable options for privacy geeks. Most likely, the native account on your device has full admin permissions by default. Many malware take advantage of this vulnerability to launch an attack.
The anonymous group behind Tunnels alleged that the materials were produced while exploring the forbidden tunnels, built underneath some of the most prestigious American Universities. No info is available on the explored institutions or how these sections can be accessed. I think it’s safe to say that these are unsanctioned exploits, all the more reason to boast them on the dark web. I have to admit to having a soft spot for Tunnels, an onion website about underground “urban” exploration. Apart from having that “As above, so below” vibe, Tunnels is a great source of info for users who are into dark urban history. The website contains pictures and videos of various cavern-like structures, shafts, and possibly escape tunnels.

Examining CSAM User Behaviour
So take this guide as you explore where to go on the Tor Browser without risking your online security. Fifty-three individuals in the U.S. were charged in the sweeping investigation, two of whom died by suicide after authorities executed search warrants on their property. The site, which had supposedly operated from at least June 2015 to 2018, had more than 200,000 unique videos, which totaled more than eight terabytes in size, according to an indictment obtained by Oxygen.com. Over the course of three years, authorities said the site received at least 420 Bitcoins through 7,300 transactions — the equivalent at the time of about $370,000. The world’s “largest” dark web child porn site, which boasted “more than a million” downloads, was shuttered after international authorities said they followed a seedy trail of Bitcoin transactions.
Blockchain even has an HTTPS security certificate for even better protection. It is the dark web’s version of Wikipedia with a massive links directory. You will find all the necessary .onion links to access any content or service on the dark web. The dark web is a hidden part of the Internet that the majority of Internet users do not think about or engage with, with the standard activities happening there varying greatly from that of the mainstream Internet. If you are engaging in the use of the dark web and have been charged with Internet sex crimes, it’s critical to work with an experienced sex crimes attorney who can help you protect your rights.
Before these children realise it, they are trapped in a world they could never imagine. He explains that the perpetrators do not work in silos, but rather as part of a larger network which makes it difficult to track down those truly in control. Depending on forum policy, “full members,” “registered members,” and “inactive members” can be distinguished. Full members have registered on the forum and meet all other requirements of membership, such as, for instance, a minimum number of posts to forum threads. Registered members have begun the process of registering on the forum but have yet to meet other requirements of membership. Finally, inactive members were once full or registered members, but have failed to meet the requirements set by the forum to maintain their membership status.
But despite an increase in productivity and the availability of new tools and technology, the IWF’s humble resources remain overwhelmed by the sheer scale of the task it faces. Of the 105,047 URLs flagged for removal by the IWF’s 13 analysts, 82 per cent were from image hosting websites. Susie Hargreaves, the charity’s CEO, criticised these sites for refusing to engage, adding that they have shown “little regard to providing safe networks, or relieving the suffering of child victims”. DARPA chose law enforcement efforts to disrupt human trafficking as a concrete cause around which it could quickly develop and deploy its new approach to searching the Internet.
- Ahmia’s .onion link is a search engine that indexes hidden services on the Tor network, allowing users to find .onion sites safely and efficiently.
- I read most of the guides on Surveillance Self-Defense, and they’re very useful — they cover everything from phishing attacks and encryption to creating secure passwords and deleting data on Windows, Linux, and macOS.
- It’s a hidden collective of sites that you could only access through a special browser.
- As authorities become more aware of the growing problem, the public is being warned to change online behaviors to prevent victimization.
About one in five forum members, however, showed an escalating or continuously high frequency of forum communications throughout much of the period the forum was online. Among those frequently communicating on the forum are many VIPs and administrators, once more underlining their importance in sustaining the online CSAM community. Studying a darknet CSAM forum—one that did not require candidate members to submit a post—Van der Bruggen et al. (2022) found that during the 8‑month period this forum was online, nearly 97% of its visitors did not communicate on the public part of the forum. These 97% accounts were classified by this research as “lurkers” or commonly referred by members of the online CSAM communities as “free-riders”—users who benefit from the community but do not contribute. However, despite so few visitors communicating, nine out of every ten forum visitors did attempt to download CSAM at least once (van der Bruggen et al. 2022).

In this way, readers across the world can still get their news without any roadblocks. The non-profit newsroom is funded by organizations such as the Sandler Foundation and has made countless contributions in the fight for free speech and privacy. The rise of cryptocurrency, and in particular Bitcoin, significantly increased the dark web’s use in illegal trade. Users could exchange funds online without sharing credit card numbers or other identifying information. In February 2011 Ross Ulbricht founded what is believed to be the dark web’s first black market, Silk Road. The U.S. Federal Bureau of Investigation (FBI) arrested Ulbricht in October 2013, but imitators still arise, many much larger.