Malicious links, phishing traps, and fake sites designed to steal your data are very common. Additionally, while the Tor Browser (the most common tool for accessing the dark web) has some built-in privacy and security features, it’s not 100% safe.. Law enforcement agencies worldwide have grappled with the challenges posed by the Dark Web, attempting to balance the need for online privacy with the necessity of combating criminal activities. If you are looking to read combating crime on the dark web online, many resources and platforms are available that shed light on the ongoing efforts to curb the growing threats of cybercrime. The Deep Web forms a more expansive but hidden layer beyond the reach of conventional search engines. This section comprises content requiring specific permissions, login credentials, or specialized tools for access.
What Is Identity And Access Management (IAM)? Benefits,
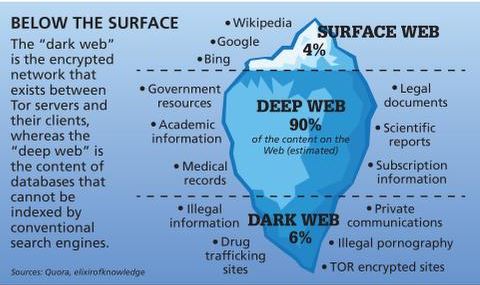
Infamous criminal sites live there, but so do popular, well-known sites and brands. I don’t recommend seeking out dark web content unless you have a specific reason to do so. If you want to observe the lawless sides of the internet from afar, check out YouTube videos of dark web explorations, like this one from John Hammond, to satisfy your curiosity. To understand how this is possible, we need to see how the web has many layers, and not all content is publicly available from a search engine query. In this guide, we’ll explain what the dark web is, how to access it safely, and why using a VPN (Virtual Private Network) with Tor is essential for anonymity.
CSO Executive Sessions: How AI And LLMs Are Affecting Security In The Financial Services Industry
For example, when you sign in to your healthcare provider’s portal to view test results or request prescription refills, you’re accessing the deep web. Furthermore, the dark web’s reputation often attracts curious individuals who are unaware of the potential risks. Casual exploration can lead to exposure to malware, scams, or illegal content, any of which could have severe consequences, both digitally and legally.
Potential Risks And Threats On The Dark Web
Remember, protecting your personal information is essential to maintaining your privacy and security while navigating the Dark Web. By following these precautions, you can significantly reduce the risk of falling victim to scams and malware on the Dark Web. To access a dark web address, you must use a VPN and a suitable browser (it should be Tor). The aim is to reduce your online footprint as much as possible, anonymize your traffic, and disguise your location. You could consider the clear or surface web the “top” and visible layer of the internet, easily accessible using a browser such as Safari, Chrome, Edge, or Firefox.
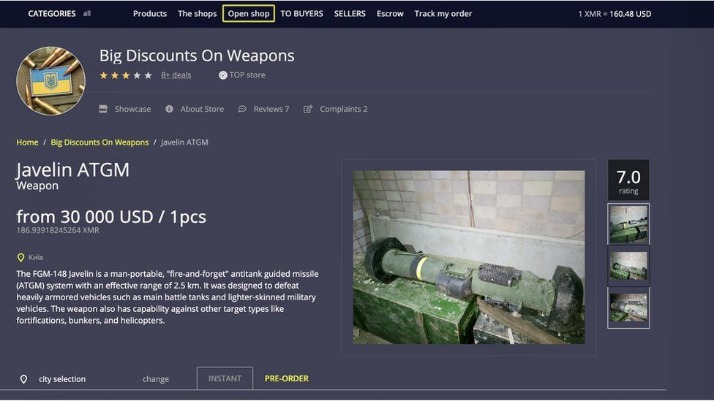
On the other hand, the dark web hosts marketplaces and forums where illegal goods and services—such as drugs, weapons, and stolen data—are traded, making it a hotspot for criminal activity. Despite its negative reputation, not all activity on the dark web is malicious; some users rely on it as a tool for freedom of expression or to circumvent restrictions. These platforms provide services related to illegal activities, such as hacking tools, malware, ransomware, or services for hire (e.g., DDoS attacks, identity theft). Some sites might offer tutorials or guides for aspiring cybercriminals. The best way to protect yourself from Dark Web dangers is to avoid involvement with it altogether. Unless you have an explicit and legitimate reason to access the Dark Web, it is advisable to stay away from this hidden realm.
Legal And Illegal Activities On The Dark Web
Privacy-focused tools like Tor, a VPN, TAILS OS, or Whonix can further enhance your security and anonymity. Yes, your ISP can see if you access the dark web, but not what you do on it. Tor traffic has a distinct fingerprint, allowing ISPs and governments to detect its usage. While they can’t see your browsing activity, some countries monitor or flag Tor users. Use a VPN before connecting to Tor (Tor over VPN) or an obfuscated bridge, which makes Tor traffic look likfe normal web traffic.
Search Darknet
These efforts could very well include accessing the dark web to help victims and hunt down criminals. While there are some threats on the surface web, and users need to browse with some level of security awareness, it’s a lot easier to stay safe on the surface web than the dark web. The surface web is what the average daily internet user interacts with the most. Search engine results from Google, Bing, and Yahoo, public websites, social media, and anything else that’s indexed and publicly available is considered a part of the surface web.
Must-Know Safety Tips For Navigating The Dark Web (If You Dare)
You’ll appreciate its added features, such as Threat Protection, which shields you from malware and trackers. NordVPN also includes Double VPN servers to double your encryption and make you untraceable. One of its key benefits is unlimited bandwidth, which sounds awesome and allows for unlimited dark web browsing. These websites will now work without issues, as the VPN hides the exit node and makes your traffic look inconspicuous. In practice, we found very little use of VPN Over Tor and saw no significant advantages.
Is The Dark Web 99% Of The Internet?
With the right knowledge and precautions, you can explore the dark web with enhanced privacy and security. After completing these steps, Tor Browser will open, and you will be ready to start browsing the internet anonymously. Tor Browser is pre-configured with privacy settings optimized for secure browsing, so you can enjoy a higher level of anonymity right from the start. To be on the safe side, we recommend combining the Tor or onion browser with a secure VPN, such as NordVPN.
These websites will also use .onion top-level domain names, and many of them will be very long, random combinations of letters and numbers. You won’t be able to access .onion addresses using a standard search engine as they aren’t indexed by crawlers. First — and this is strongly recommended — you should install a Virtual Private Network (VPN). Also, you need to use a privacy-focused browser such as the Tor network to connect via nodes and proxy servers, which are more secure and aim to anonymize traffic requests.
It works by routing your encrypted traffic through multiple volunteer-operated servers, known as onion routers. Tor is by far the most widely used dark web network and is the biggest network in terms of content and activities. I2P, or the Invisible Internet Project, is an anonymous network layer to facilitate secure and private communication among its users. It works as a decentralized, peer-to-peer network that emphasizes censorship resistance and complete anonymity. The dark web often connotes illicit activities like illegal drug sales and hacking.
- Yes, your ISP can see if you access the dark web, but not what you do on it.
- It is now one of the most widely used browsers to access the dark web.
- Relays help route traffic securely by passing encrypted data through multiple nodes before reaching its destination.
- Cybercrime services, such as hacking tools and stolen databases, are available for hire, creating a marketplace for illicit online activities.
- Visiting a dark web site requires specialized software like the Tor Browser, which routes traffic through a series of random relays across the globe to mask both origin and destination.
- Open up Tor, and you won’t suddenly see the dark web staring back at you.
Stay In Touch With Us
Public websites indexed by search engines (e.g., news sites, social media, blogs). The Tor browser is designed to provide improved online anonymity and security. However, be careful when using the Tor Browser to access the dark web. The dark web is a dangerous place, and all bets are off on your safety. This is why I strongly advise anyone visiting the dark web to exercise the greatest of caution during their dark online travels. Check out my article for more information about the dark web and how to access it while staying safe.



