The Tor Browser is a specific web browser, based on Firefox, that utilizes the Tor protocol to enable private browsing. Tor routes data through at least three servers, and websites will only see the IP address of the last server, not yours. It has features to maximize your privacy, unlike standard web browsers that have less stringent privacy protections. However, using Tor has some challenges that you should be prepared for.
Is Accessing The Dark Web Illegal In India?
Accessing the Dark Web safely in 2025 demands vigilance, preparation, and strict adherence to security best practices. By carefully following the safety procedures outlined in this guide, you minimize your risk of encountering malware, fraud, or legal troubles. Always remember, your safety online depends significantly on personal responsibility, informed decisions, and proactive application of security tips. Embrace these strategies to confidently navigate the Dark Web, preserving your privacy and security in an ever-evolving digital landscape. Lokinet is easier to set up than I2P, and it may run faster than Tor in some cases, especially when visiting regular websites through its secure network.
- Justice has acquired extensive content writing experience over the years.
- Tor Browser masks your IP address and routes traffic through multiple servers.
- These onion addresses will remain online even if the original page disappears.
- Antivirus is a great way to stay protected while using the Tor browser or the dark web.
- Browsing via Tor is significantly slower than navigating the Web with a standard browser.
- Launch the Tor Browser from your desktop or Start menu, then click Connect on the welcome screen to establish a secure connection to the Tor network.
Disgruntled Developer Gets Four-year Sentence For Revenge Attack On Employer’s Network
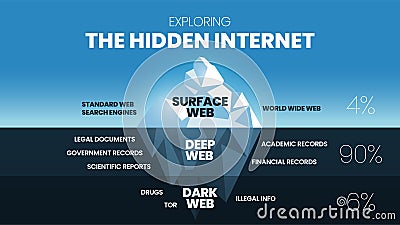
As noted by Andy Greenberg at Wired, while the deep web makes up approximately 90% of the internet, the dark web makes up only around 0.1% and is designed to provide anonymity for users and site owners. In darknet mode, you can select friends on the network and only connect and share dark web content with them. This enables individuals to form groups and only share content in a highly anonymous network of darknet users who they know. The advantages of I2P are based on a much faster and more reliable network. Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains.

There’s a significant risk to dark web users of being exposed to malware (malicious software) infections. There are several programs that hackers frequently use on the dark web. On top of that, the installation process of Freenet is rather easy. Simply download the file, install the software, and you’re ready to use its web-based interface. Opennet connections are easier to use, but darknet connections provide more security against attackers on the network.
Tor Over VPN Vs VPN Over Tor: Which Should You Use?
You might want to hide your Tor Browser download using a VPN and your existing browser’s private/incognito mode. The dark web, or dark net, is a small part of the deep web that is kept hidden on purpose. Websites and data on the dark web do typically require a special tool to access. Despite its relatively high profile, the dark web makes up a vanishingly small portion of the World Wide Web, perhaps less than 0.01 percent. By distributing communication over several nodes, it obscures the user’s IP address. Indeed, most nations; including the United States, the United Kingdom, and India, allow access to the dark web as a lawful activity.
- Hence, you never know when a popular .onion site is going to vanish, or even die.
- Since Hidden Wiki maintains all kinds of websites, ensure you don’t open something you don’t want to see.
- Malicious actors and government agencies can run Tor nodes, compromising privacy and security.
- Each one offers unique features, such as better privacy and extensive .onion site indexing.
- The platform stood out during my testing for its commitment to anonymity — all messages are fully encrypted and stored on a decentralized network.
Quick Links
Tor hides users from anyone who might be watching, whether it’s an Internet service provider (ISP), the government, advertisers, or cybercriminals. Tor’s data encryption attracts anyone who wants to keep their activity hidden, regardless of their motives. Tor is a free software platform designed to protect users” identities while browsing the Internet.
Is Tor Browser Safe To Use?
You can buy credit card numbers, all manner of drugs, guns, counterfeit money, stolen subscription credentials, hacked Netflix accounts and software that helps you break into other people’s computers. Buy login credentials to a $50,000 Bank of America account, counterfeit $20 bills, prepaid debit cards, or a “lifetime” Netflix premium account. Yes, some can use the dark web for good reasons, like whistleblowers and journalists, and the dark web offers them anonymity. But you must not use it for any illegal or illicit activities or discussions.
Best Online Cyber Forensics Courses For Beginners
The Tor network understands these addresses by looking up their corresponding public keys and introduction points from a distributed hash table within the network. It can route data to and from onion services, even those hosted behind firewalls or network address translators (NAT), while preserving the anonymity of both parties. Tor is necessary to access these onion services.59 Because the connection never leaves the Tor network, and is handled by the Tor application on both ends, the connection is always end-to-end encrypted. Despite the anonymity features of Tor Browser, users should also be aware of the potential for surveillance and tracking. While Tor makes it significantly harder to trace online activities, it does not guarantee complete anonymity. Internet service providers may also be suspicious of Tor usage and might monitor traffic patterns, even if they cannot see the content of the encrypted communications.
Deep web content includes anything behind a paywall or requires sign-in credentials. It also includes any content that its owners have blocked web crawlers from indexing. Businesses need monitoring activities in place, but at the same time, they should ensure that the monitoring complies with and adheres to all laws and regulations for implementing dark web monitoring.
The email service is available both on the surface and on the dark web. The goal of an anonymous and privacy network, Tor, is not to engage in the extensive collection of data. However, data is required for understanding, monitoring, and improving the network. Furthermore, data will help to detect attacks against the network and possible censorship events.
Never install extensions or additional add-ons, even if they seem useful. They change your browser fingerprint and make you easier to track. The Hidden Wiki is a popular onion link directory on the dark web offering categorized lists of sites. Secure communication for journalists, accessing privacy-focused forums, and whistleblower submissions. Tor encrypts your traffic and routes it through multiple volunteer-operated relays, making it difficult to trace.
All this activity, this vision of a bustling marketplace, might make you think that navigating the dark web is easy. The place is as messy and chaotic as you would expect when everyone is anonymous, and a substantial minority are out to scam others. There are also many tools that can be use to monitor the dark web and scan for personally identifiable information and even respond to attacks.



