
The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers. Later on, the underlying Tor code was released into the wild under a free license, leading to the formation of the Tor Project. In 2008, the first Tor Browser was released, making it easier for any internet users to access the dark web. In 2002 the dark web began to grow significantly when researchers backed by the U.S. The Tor Network provided a way to open safe communication channels for political dissidents, while also offering a channel for American intelligence operatives to communicate from around the globe.
Securely Offline Yourself From Dark Web
If the new company gets hacked or otherwise fails to protect your information, that data could end up on the dark web. “Follow the money,” the source known as Deep Throat says in the film adaptation of All the President’s Men. “Always follow the money.” In the same vein, you should always follow your data, particularly after a company files for bankruptcy or in the aftermath of a data breach. While researching, I learned that there are many paths our personal information can take on the journey from your computer to the dark web. A more general concern is that even relatively low-level credentials can be used in conjunction with other data to build a picture of the individuals using the MOD portal. According to the i news site, the stolen credentials were for the MOD’s Defence Gateway website, a non-classified portal used by employees for HR, email and collaboration, and education and training.
The CSO Guide To Top Security Conferences
The thefts are ongoing, with 124 compromised credentials said to have been detected during 2024. The login credentials of nearly 600 employees accessing a key British Ministry of Defence (MOD) employee portal have been discovered circulating on the dark web in the last four years, it has been reported. Never miss the biggest stories with breaking news alerts in your inbox. Well, there’s a reason why it’s recommended to browse with a minimized or rescaled window – you can be tracked based on your active window’s dimensions (yeah, they really can do that).

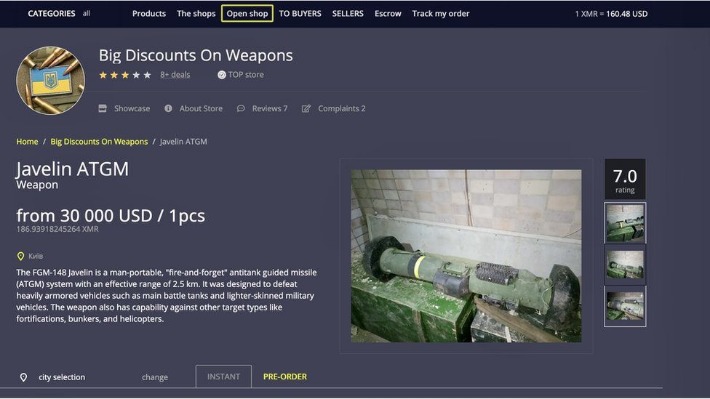
Remember, do not get too focused on websites selling products at low rates or with packages. Also, deal with the seller through websites and do not send payments outside it. Also, you should regularly look for updates for your Tor and VPN software to experience secure browsing.
What Should You Do If Your Data Has Been Leaked In A Breach?
If you make use of a password manager, then it may come with a feature that monitors the dark web for mentions of your email address and password, or any other personal details. It’s something built into the password management services offered by Apple and Google as well, so you don’t need to trawl through data leaks manually yourself. Apart from the dark web markets that are operating online today, some raided platforms influenced many markets. Active for a decade since 2014, it is a widely used credit card shop used to source stolen credit card information such as dumps, CVVs, Wholesale Accounts.
Legitimate Use Cases For The Average User
It supports operations in multiple languages and operates on both clearnet and Tor. The use of this network has been prohibited in the United Kingdom since November 2014. The Digital Economy Act 2017 requires ISPs to prevent access to these sites and have agreements with foreign countries in order to enable enforcement of these rules. The laws in this case work not against the average user, but against the creators of blocking tools and providers. For example, the Tor browser is not banned in the UK, as it makes it possible to bypass blocking.
Countries With The Most Stolen Data Per Person
- Again, people who live in countries where the freedom of the internet is limited, for example in China, can really benefit from using Tor.
- Information may be published through a number of different online platforms which are accessible to others, including social networking sites, multi-player gaming portals and other web-based forums.
- Russian Market has consistently remained one of the most popular and valuable data stores on the dark web.
- Dark web is not safe to browse without a VPN, as it leaves traces of your identity.
- It might sound weird that Google doesn’t index these pages, but it does carry some logical sense.
Also known as an “exhaustive key search” – essentially it consists of systematically checking all possible keys or passwords until the correct one is found. An organisation’s strategy or policy that allows employees to use their own personal device for work purposes. An algorithm is a procedure used for solving a problem or performing a computation. Algorithms act as an exact list of instructions that conduct specified actions step by step in either hardware-based or software-based routines.
It offers its users secrecy and makes it very difficult to track their activities. This has led to it becoming a marketplace for selling drugs, stolen data and weapons. One of the most significant dangers of the dark web is the risk of encountering criminals. Illegal drugs, stolen information, counterfeit money, weapons, and even human trafficking are readily available for purchase. Interacting with these criminals can lead to a range of personal and financial harm, including identity theft and fraud. The dark web, a hidden part of the internet that requires specific software to access, poses potential risks to individuals who choose to browse its content.
Malicious Software
It is considered very secure thanks to strict user validations and transparent payment and vendor review procedures. You can get a fine or prison sentence if you are found guilty of taking, carrying, making or dealing (also called supplying) illegal drugs. Offences under the Protection of Children Act 1978 include taking, permitting to be taken and making child pornography, distributing child pornography, or possessing child pornography. If anyone is found guilty of committing these sexual offences, they could face a maximum possible sentence of 10 years’ imprisonment.
Use cryptocurrency to buy anything, and use a disposable email address for any type of communication on the dark web. Check around with other users and ask if they know anything about the new marketplace. Government cyber teams can take such websites down, arrest the owners and then use the website to track and follow users that show activity on the website. The dark web is also a place for scammers to attract vulnerable and unwitting victims.

It adds an extra encryption layer and passes your traffic through a secondary server of your choice, preventing anyone from seeing that you are accessing the web via Tor. You should never use your personal information on the dark web anywhere else in your life. Ensure you have used prepaid and unidentifiable credit cards when purchasing on the dark web. While Tor offers anonymity on the dark web, your online activities leave breadcrumbs that can reveal your identity. That is why you should only use a reliable VPN like ExpressVPN or NordVPN for additional security and privacy. Many dark net sites do not undertake the necessary measures to protect users like most websites on the surface web.
- The figure is slightly higher for those who are active gamers, it added, with one in four exhibiting illegal behaviors.
- Supreme Court will allow the FBI to search and seize any computer that’s using the Tor browser or VPN.
- For example, you can find information unavailable to the public and share data privately while protecting your online identity.
- The Obscene Publications Act 1959 (‘OPA’) was amended to deal with electrically stored data or the transmission of that data.
Here are some of the now-defunct dark web markets that were notorious for cybercrime. Launched in September 2022, Torzon Market operates on the Tor network and features over 11,600 illegal products, including drugs and hacking tools. It enhances buyer transparency by importing vendor feedback with PGP proof. Torzon offers a premium account option for additional benefits and is valued at approximately $15 million, accepting payments in Bitcoin (BTC) and Monero (XMR). WeTheNorth is a Canadian market established in 2021 that also serves international users. It offers counterfeit documents, financial fraud tools, hacking and malware services.

Note that engaging with the content in any way is not only distressing but could also put you at legal risk. This is because law enforcement often actively monitors these sites. These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship. The anonymity provided by onion routing comes at the cost of slowing your internet considerably. As such, we do not recommend using Tor if you want to do data-intensive activities like streaming in HD, gaming, torrenting, or making video calls.



