However, it’s important to note that this built-in VPN is not designed to connect directly to the Tor network or .onion sites. For general privacy on the clear web, it’s a really good option. But it’s recommended that you stick to Tor Browser still for true dark web access. For example, many things can go wrong if you try to change any settings inside the browser, including exposing your private browsing information on the dark web. But if you still want to crack on, we’ve previously looked at how to install and use the Tor browser and find onion sites you can visit without getting into trouble.

How Much Does It Cost To Use Tor Browser?
So, you’ll be happy to know there are several easy ways to delete a page in Word, including both blank pages and those you simply no longer need. The internet is huge—even in its shadows—it is possible to wander legally there. Due to compatibility issues and technical restrictions imposed by Apple, Tor browser isn’t available on iPhones that haven’t been jailbroken. Onion Browser is typically the go-to alternative for iOS devices and is powered by Tor.
Onion Links: How To Access Them

Because Tor over VPN puts your privacy in the hands of the VPN provider, it’s important to choose one with a strict no-logs policy, meaning it doesn’t store user data. ExpressVPN is my top recommendation for Tor VPNs because it’s fast, easy to use, and its no-logs policy has been independently audited and confirmed by third-party cybersecurity experts. While the dark web comes with risks, it’s possible to explore safely if you take the right precautions. By following some basic security tips and using the right tools, you can greatly reduce your chances of running into trouble.
- Tor for Android is developed by the Tor Project itself, while the Onion Browser is the recommended option for iOS users.
- If top-notch privacy is your goal, yes, you can use the Tor Browser for all of your browsing.
- Access any site you want as you normally would on your regular browsers.
- We must explain that Tor is safe on paper but practice has shown that this browser can fail you.
Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more. Before you embark on your journey into the Dark Web, it’s crucial to establish a secure foundation. While the Tor network is designed to provide anonymity, it alone cannot guarantee your privacy or safety. This section will guide you through the essential preparatory steps and tools to ensure that you remain as protected as possible while exploring hidden services and tor onion domains. I2P is a privacy-focused dark web browser that emphasizes secure peer-to-peer connections.
So, sites that contain a domain extension like .com, .org, .net, .biz, .info, etc. can be found on the surface web. In addition, the content on the pages don’t need any special or custom configuration to access. Did you know that Google only shows you a glimpse of all the websites that actually exist? The last time I checked, it’s estimated that the entire web is roughly 500 times larger than what Google returns in Google Search.
More On How To Stay Safe On The Dark Web
We recommend you only visit safe dark web links to explore such as The CIA, Facebook, DuckDuckGo, and Torch. Many services that are allegedly offered on the dark web are scams. Some services are genuine; you can get what you want at an agreed fee. Furthermore, it’s critical to understand that Whonix is not a stand-alone browser. It is a component of Whonix, an operating system that functions as a whole inside a virtual computer.
Cybersecurity Best Practices For Protecting Your Digital Assets
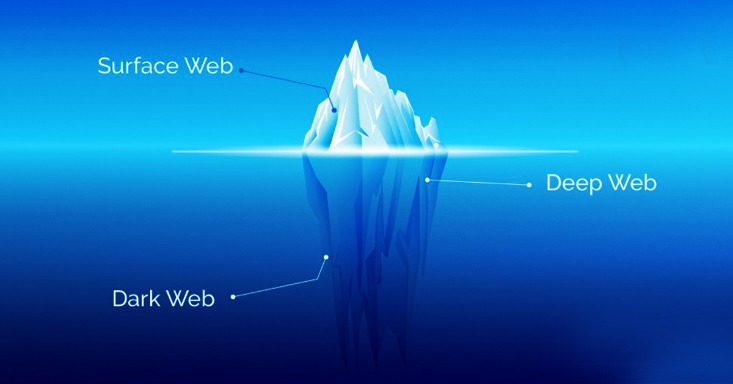
The dark web is a playground for hackers, cybercriminals, and people with nefarious objectives. We strongly advise you against visiting it, even if your intentions are good. Contrary to a widespread misconception, the dark web is a tiny part of the web. According to Recorded Future research1, out of 55,000 onion domains discovered, only 8,400 have a live site. Knowing about various types of ransomware and common hacks can help you better prepare to spot cybersecurity threats on the dark web. For example, your Geekflare.com—your trusted business resource for growth exists on the surface web.
Extra Layer Of Protection Against Exit Node Snooping
Downloading anything online can be dangerous, let alone the hidden internet. Fun fact is that Tor Browser (Tor network is a different thing than the browser) is built from Firefox ESR (Extended Support Release), a modified version of Firefox. So, it’s worth using Firefox if you’re up for the tweaks needed.
Best Data Science Jobs In India High-Salary Roles For IT Infra, Cyb
Traders cash in on stolen credit card data dumps, initial access points to vulnerable systems, credentials, and intellectual property belonging to companies compromised during cyberattacks. Our editors thoroughly review and fact-check every article to ensure that our content meets the highest standards. If we have made an error or published misleading information, we will correct or clarify the article. If you see inaccuracies in our content, please report the mistake via this form.
It’s something built into the password management services offered by Apple and Google as well, so you don’t need to trawl through data leaks manually yourself. Hackers spend a lot of time on the dark web, and it’s not too difficult to get access to hacking tools and data leaks in this part of the internet. However, it’s much harder to get at the people who are doing the uploading and downloading. Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails.

Step 7: Browse The Dark Web With Tor
Our experience has shown that this is the #1 way of doing things without risking your privacy. We understand that because of the reputation looming over the dark web as being so dangerous, mysterious, and whatnot. Some sites are safe to use, especially those where you don’t need to provide sensitive information to use. Private Internet Access even offers the Shadowsocks proxy for added security. There’s also MultiHop that boosts your encryption, along with MACE which blocks tracking. PIA doesn’t pull punches, so it strikes back against its competition with a proven-in-court no-logs policy, split tunneling, and even port forwarding to diversify its apps.
- Unlike Tor and I2P, a server is not needed to host content, and the content that you upload on Freenet stays there permanently.
- So if you’re ultra-paranoid about tracking, this one’s best reserved for lighter, less sensitive sessions.
- Many sites become defunct quickly, either because they are shut down due to illegal activity, their founders lose interest, or they change addresses and names to avoid detection.
- Visiting .onion forums or encrypted marketplaces isn’t a crime on its own, but accessing illicit content, buying restricted items, or interacting with criminal services definitely is.
- It encrypts your traffic right away, which is beneficial if you don’t want your ISP to see you’re using Tor.
- If you must use one, ensure it’s a VPN with a strict, independently audited no-logs policy.
The trick with these onion websites is their accessibility, which is made possible only with Tor. Tor is an abbreviation for The Onion Router and now, we can see why. Bitcoin is the most widely recognized and utilized cryptocurrency on the dark web. The free version also includes basic malware protection, which is a nice bonus considering how sketchy some dark web sites can get.
What Does Tor Browser Do?
Now that you’re connected to Tor, you’ll need a dark web search engine to help you find .onion sites. Unlike regular websites, .onion sites have complex, hard-to-remember URLs that you can’t find using regular search engines like Google. Whether your search engine of choice is Google, Bing, Baidu, Yahoo! The true internet – that which includes content not indexed by these search engines – is hundreds of times bigger.



